LMG Researcher Uncovers 3 New Critical Zero-Days: CU Solutions Group Vulnerabilities Impact All CUSG CMS Users
 Finding vulnerabilities before hackers do is our penetration testing team’s overarching goal. With software exploits serving as the initial intrusion point for 32% of attacks with known causes, pentesting is one of the best ways we can protect our clients. When our team finds zero-day vulnerabilities, such as the one LMG Security’s Cybersecurity Consultant Emily Gosney found in a popular vendor web application, we get to help make everyone safer. During a routine penetration test, Emily discovered a critical vulnerability in the CU Solutions Group (CUSG) CMS product, which is used by hundreds of financial institutions. In good news, CUSG now reports that this issue has been remediated. Even if you are not impacted by these CU Solutions Group vulnerabilities, read on as this is also a great penetration testing case study on how vulnerabilities are found and reported.
Finding vulnerabilities before hackers do is our penetration testing team’s overarching goal. With software exploits serving as the initial intrusion point for 32% of attacks with known causes, pentesting is one of the best ways we can protect our clients. When our team finds zero-day vulnerabilities, such as the one LMG Security’s Cybersecurity Consultant Emily Gosney found in a popular vendor web application, we get to help make everyone safer. During a routine penetration test, Emily discovered a critical vulnerability in the CU Solutions Group (CUSG) CMS product, which is used by hundreds of financial institutions. In good news, CUSG now reports that this issue has been remediated. Even if you are not impacted by these CU Solutions Group vulnerabilities, read on as this is also a great penetration testing case study on how vulnerabilities are found and reported.
UPDATE: After this announcement, CU Solutions Group (CUSG) contacted LMG Security to share the good news that they had already pushed out an update to all CUSG CMS product users that remediated all three vulnerabilities listed in this 2/13/24 press release. CUSG also shared that they will add new proactive prevention processes to further enhance their security moving forward. This serves as a good reminder that routine penetration testing is a best practice to catch these security gaps before a breach, especially in commonly overlooked web and cloud applications.
Discovering the CUSG Vulnerabilities
In late October of 2023, LMG’s Emily Gosney was conducting a web application penetration test for one of our clients: a credit union whose public-facing website is powered by the CU Solutions Group (CUSG) Content Management System (CMS), which is a content management system tailored for credit unions. CUSG is an award-winning provider of technology-driven credit union solutions, but security gaps happen to everyone—Microsoft just had a SharePoint vulnerability last month that criminals could leverage to get admin privileges. As Gosney began testing the web app, she discovered that client’s CUSG CMS had zero-day vulnerabilities that impacted not only the security of our client, but the security of hundreds of CUSG CMS customers. Read on to learn how Gosney made these discoveries and learn more about the vulnerability reporting process in what has turned into an informative penetration testing case study.
The Zero-Day Discovery and Reporting Process
The test began as a “black box” penetration test—in other words, Gosney started from the Internet with no special access or credentials. Initially, it appeared to be an average penetration test with typical minor findings. However, after Gosney performed directory brute forcing to discover hidden URLs, she found an admin login page located at “/admin”. This is a very conspicuous location, so it was easily guessed, and Gosney was able to identify a Cross-Site Scripting (XSS) vulnerability on the login page.
XSS on login pages—especially those for admin interfaces—is particularly dangerous as it provides an environment that is ripe for credential harvesting. A malicious actor could launch a very convincing spear phishing campaign linking victims to their own company’s webpage, which most employees would believe is safe to click. Upon clicking the link and entering their credentials, the malicious JavaScript code supplied in the phishing link would then siphon the credentials and send them back to the malicious actor.
LMG’s client could not create an account for the penetration testers to examine the admin portal, so they reached out to CUSG to have a new account provisioned. CUSG responded quickly and provided LMG with a basic account with the absolute minimum privileges. It is important to note that CUSG can log in to its customers’ CMS portals to perform admin tasks.
Gosney knew she had to be extremely careful testing the CMS admin portal since there was a high risk of defacing or deleting pages on a live production website. After performing careful reconnaissance, she compiled a list of URLs that she could test with minimal risk.
She began by scanning the admin portal for SQL injection, as the CMS is written in PHP which is disproportionally affected by SQL injection vulnerabilities compared to other programming languages. While PHP is a powerful and flexible language, it’s very easy to accidentally code a vulnerability when using it.
Uncovering a SQL Injection Vulnerability
The very first page Gosney chose to test—an HTTP GET request for the page editor on a draft page—was identified by ‘sqlmap’ as being vulnerable to SQL injection via two methods known as “boolean-based blind” and “time-based blind.”
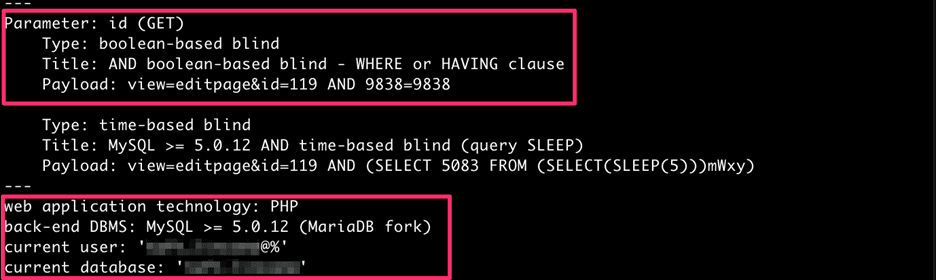
A screenshot of the initial entry point.
Finding Backdoor Admin Accounts
Using ‘sqlmap’, Gosney was able to exploit this SQL injection vulnerability to enumerate the database version, the current database, the current user, and 226 tables within the database. Within this data, Gosney discovered the “taft_user_master” table which contained the backdoor accounts that CUSG employees use to log in to their customers’ CMS installations.
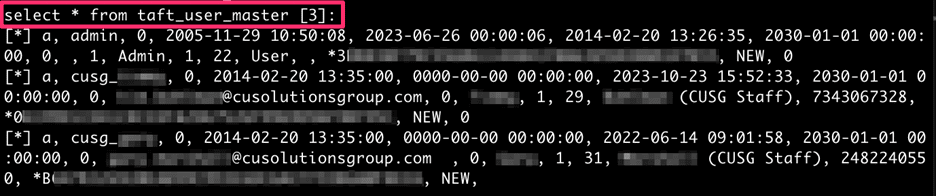
A screenshot of the “taft_user_master” table where accounts were uncovered.
Among the various “CUSG Staff” backdoor accounts, Gosney found a 20-year-old admin account (conspicuously named “admin”). Since LMG’s client only began using the CUSG CMS about three years ago, Gosney concluded that this table is populated during the CMS installation process when initializing the database schema. This means that every CMS installation worldwide has an identical table of hard-coded backdoor accounts with the same passwords.
These passwords are cryptographically scrambled—or what we call “hashed”—so we have no way of knowing what the actual passwords are by looking at this data. However, if someone were to crack any one of these password hashes, they would be able to authenticate to the admin portal of any credit union that uses CUSG CMS with privileges greater than those that CUSG grants to its customers.
Cracking the Backdoor Account Passwords
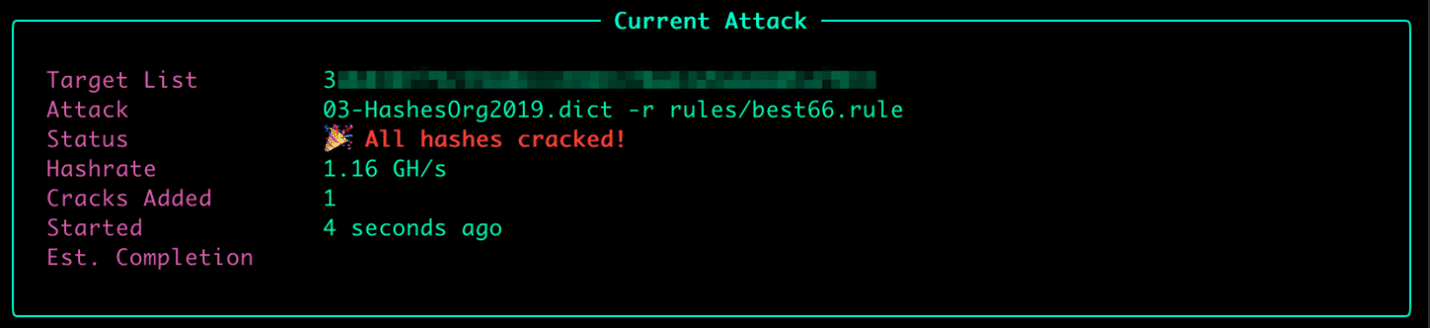
Gosney was able to crack this password in just four seconds, as shown in the figure above.
Due to the significance of these accounts, it is imperative that CUSG use long, randomly generated passwords that cannot be cracked. However, the password for the CUSG “admin” account can be found verbatim in the “Hashes.Org 2019” wordlist, a popular resource comprised of passwords that have been cracked in various data breaches.
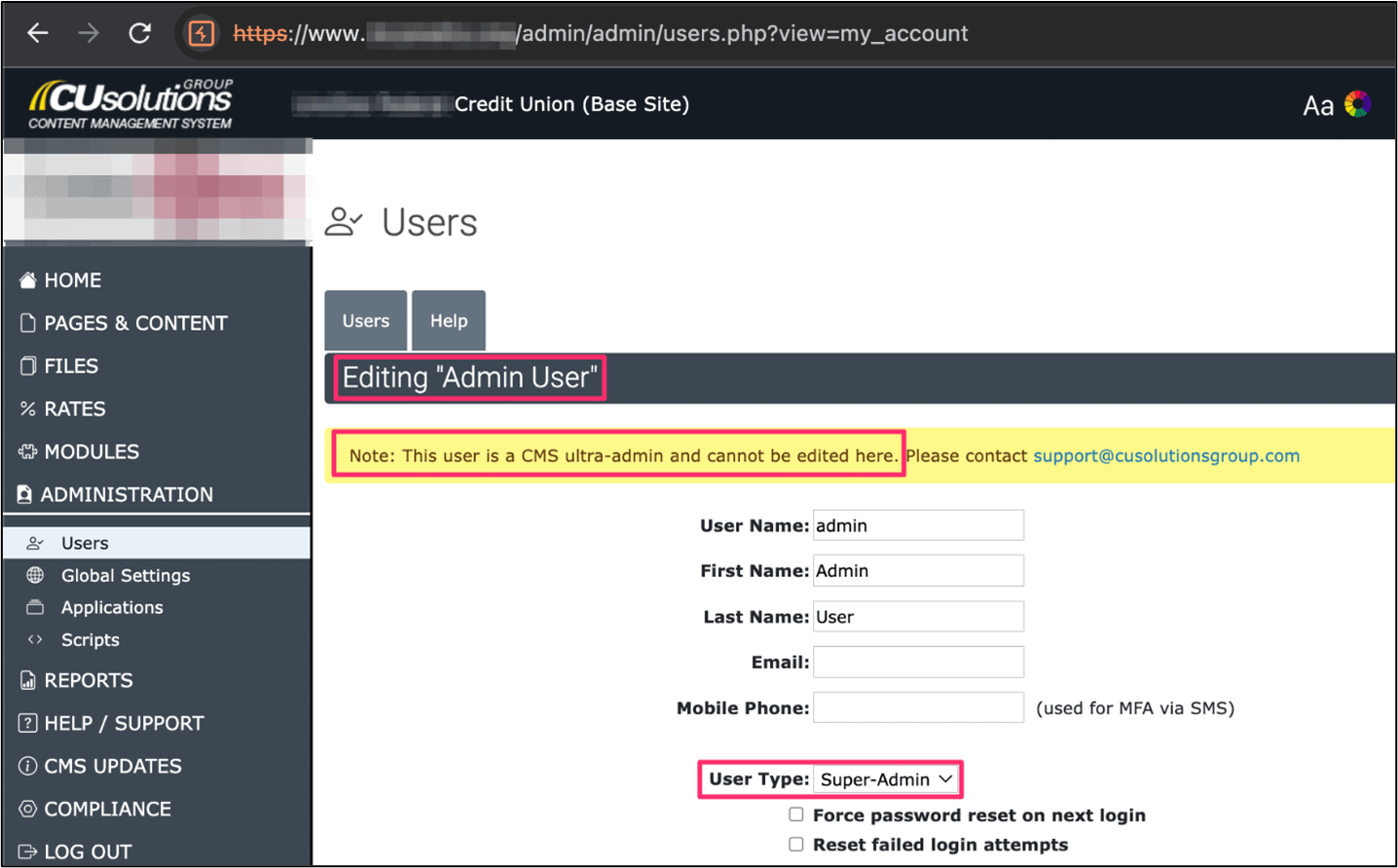
Screenshot of Gosney attaining “ultra admin” access.
Notification and Support for Resolution
Upon discovering this fundamental security flaw, Gosney immediately halted testing and notified LMG’s client of her findings. Gosney met with the CU Solutions Group staff to review the vulnerabilities and provided them with a written summary of technical details.
Gosney also reported these findings to the Common Vulnerabilities and Exposures (CVE) program for tracking, and the following CVE numbers were assigned:
CVE-2023-48987: A blind SQL injection vulnerability in ‘pages.php’ within the CMS admin portal could enable an authenticated malicious actor to gain full read/write access to the backend database. A malicious actor could leverage this vulnerability to obtain the password hashes for the backdoor “ultra admin” accounts from the “taft_user_master” table, which would grant access to every CMS installation.
CVE-2023-48985: A reflected cross-site scripting vulnerability in ‘login.php’ could enable an unauthenticated malicious actor to intercept login credentials for the CMS admin portal. This vulnerability could be chained with CVE-2023-48987 to form a complete “zero to admin” kill chain.
CVE-2023-48986: A reflected cross-site scripting vulnerability in ‘users.php’ within the CMS admin portal could enable a malicious actor to trick an authenticated user into unintentionally performing privileged actions within the admin portal.
CUSG Customers Should Take Immediate Action
“The ‘ultra admin’ account is a vendor backdoor account that grants access to every installation of CUSG CMS globally, so just one organization running an outdated version of this application can put all other users at risk, including those who are already running the latest version,” Gosney continued. “It’s crucial that impacted organizations take immediate action to protect themselves from a data breach by not only keeping their software up-to-date, but also by enabling multi-factor authentication to prevent malicious actors who possess the ‘ultra admin’ password from logging into the CMS portal.” By our estimation, over 200 credit unions are impacted by these vulnerabilities.
Organizations impacted by the CUSG vulnerabilities should immediately:
- Upgrade to the latest version of CUSG CMS. CUSG released CMS v7.75 shortly after we reported these vulnerabilities, so upgrading to v7.75 may address these vulnerabilities, but you should check with CUSG for complete information on updates and any additional remediation directions. At the time LMG published this blog, CUSG did not confirm this information.
- Enable multi-factor authentication (MFA) immediately. THIS IS CRITICAL. As Emily Gosney pointed out above, even if you upgrade to v7.75, you are still not fully protected. Even one organization running an outdated version can give attackers access to a backdoor admin password that works for all CMS installations. If you’re a regular reader of our blogs, you know that enabling strong MFA whenever possible is an inexpensive way to reduce your risk of a breach. Check out our recent authentication blog for an update on MFA and passwordless authentication trends for more information.
- Tighten your security and monitor for signs of irregular activity. You can also read our guide on zero-day attack response for more information.
UPDATE: After this announcement, CU Solutions Group (CUSG) contacted LMG Security to share the good news that they had already pushed out an update to all CUSG CMS product users that remediated all three vulnerabilities listed in this 2/13/24 press release. CUSG also shared that they will add new proactive prevention processes to further enhance their security moving forward. This serves as a good reminder that routine penetration testing is a best practice to catch these security gaps before a breach, especially in commonly overlooked web and cloud applications.
The Seriousness of Zero-Day Vulnerabilities and Getting the Word Out
This web application penetration testing case study and discovery underscores why it’s so important that ALL organizations have annual pentests that include their web apps and cloud environments. These CUSG CMS vulnerabilities impact hundreds of organizations, primarily credit unions. You may be wondering why we just issued a press release today if we found this vulnerability several months ago. This is a standard responsible disclosure policy. We immediately reported these vulnerabilities to CUSG and the CVE program and provided greater than the standard 90-day window to enable the software provider to fix the issue before disclosing this vulnerability.
Zero-day vulnerabilities are a top cybersecurity threat (read our guide on the 6 Top Cybersecurity Threats of 2024 for more information) and are difficult for organizations to protect themselves against, but please check out our guide on zero-day attack response for both response and proactive prevention advice. Software vulnerabilities are an industry-wide problem that impacts all of us. Finding and reporting these vulnerabilities helps providers close these security gaps and increases awareness about why all organizations need a strong patch management program, continuous vulnerability management, and an EDR/XDR solution to reduce risk.
We hope you found this information on the CUSG vulnerabilities helpful, whether you are an impacted organization or read this as an informative penetration testing case study. Please contact us if you need any additional help with remediation or proactive cybersecurity testing, advisory services, solutions, or training.
