Double Trouble: Understanding Two Cisco Zero Day Vulnerabilities & Guide to Zero Day Attack Response
 Another day, another zero-day exploit—or at least it feels that way. With 55 zero-day vulnerabilities exploited last year and software exploits serving as the initial intrusion point for 32% of attacks with identified causes, zero-day exploits are a top attack vector. Two of the latest critical zero day vulnerabilities impact Cisco and its customers. Let’s look at the timelines for these Cisco zero day vulnerabilities, and then dive into a step-by-step zero-day attack response checklist.
Another day, another zero-day exploit—or at least it feels that way. With 55 zero-day vulnerabilities exploited last year and software exploits serving as the initial intrusion point for 32% of attacks with identified causes, zero-day exploits are a top attack vector. Two of the latest critical zero day vulnerabilities impact Cisco and its customers. Let’s look at the timelines for these Cisco zero day vulnerabilities, and then dive into a step-by-step zero-day attack response checklist.
Last month on October 16th, Cisco disclosed a critical vulnerability, CVE-2023-20198, with a critical CVSS score of 10. But that’s not all—just four days later, on October 20, another alarming vulnerability, CVE-2023-20273, was revealed. These vulnerabilities have given hackers a foothold to exploit over 40,000 devices and raised concerns about the potential consequences for numerous organizations, vendors, and partners.
Understanding the New Cisco Zero Day Vulnerabilities
What are the potential security gaps for these new Cisco zero day vulnerabilities? The first vulnerability, CVE-2023-20198, is a level 10 critical threat. When exploited, it grants hackers the keys to the kingdom, allowing them to gain a privilege level 15 (admin) account and issue level 15 commands without the need for authentication. Yes, that phrase should make all of us shudder. This vulnerability enables attackers to create local user accounts with normal privileges and, perhaps more frighteningly, enables them to remotely log into the compromised devices and infiltrate and compromise network infrastructure.
The Second Punch Impacts iOS and Beyond
As if one major vulnerability wasn’t enough, Cisco’s woes deepened with the revelation of CVE-2023-20273 on October 20th. This second Cisco zero day vulnerability pertains to the WebUI and allows attackers to break free from the confines of iOS and access the underlying Linux OS.
Once inside, the hackers can execute arbitrary commands on the OS as the root user, which is the highest level of privilege, providing them with tremendous control. It also enables them to install a persistent backdoor, creating an enduring presence on the compromised devices. In addition, when the attackers installed this LUA backdoor, cybersecurity teams were running a simple query to see if the backdoor was there. So, the attackers changed it by altering their programming to try to evade detection. This also forced researchers to pivot and change their query to look for another indicator of compromise.
These Cisco zero day vulnerabilities are just another in a string of unpredictable zero day cybersecurity risks. So, how do you combat these risks? Let’s dive into our zero day attack response checklist to share some response steps.
 Zero Day Attack Response Checklist
Zero Day Attack Response Checklist
It’s not a matter of if you will face a zero day attack, it’s a matter of when. Preparing in advance can speed identification and reduce your financial and reputational damage if you are breached. To help you prepare, here’s a step-by-step zero day attack response checklist.
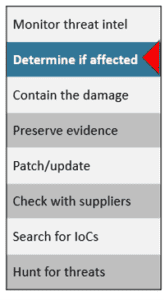
1. Monitor Threat Intelligence. Your technical or security teams should regularly monitor threat intelligence. There are many different free and paid threat intelligence options including the CISA Known Exploited Vulnerabilities Catalog, our favorite free resource. We recommend checking threat intelligence daily, or at least weekly, and keeping an eye on vendor alerts and cybersecurity news for zero day exploits. You can also watch for alerts from your suppliers, social media, security vendors, cybersecurity news outlets, and more. If you have locations or partners in the European Union, you should also monitor the Information Sharing and Analysis Centers (ISACs) alerts.
2. Determine If You Are Affected. Start by determining if you are using the vulnerable software and the affected version. Sometimes this is not immediately known during the initial zero-day report. If you are not sure what version of the software you’re running, you can also check your change management logs to confirm. While the two Cisco zero day vulnerabilities above were well defined, sometimes you may not be sure if you are impacted by a specific zero day vulnerability. In these cases, you need to plan ahead by checking your software data inventory (an SBOM is even better if you have it), watch for changes in your environment, and continue to check with you suppliers in case their vulnerabilities open a security gap into your network.
3. Contain the Damage. Act quickly but carefully to minimize the risk of data theft and further compromise. Look for vendor or government advisories for specific strategies, but some general next steps can include:
- Restrict inbound and outbound traffic
- Yank the network/power
- Perform a system-wide password reset
However, keep in mind that fast containment strategies can have operational impacts, depending on the criticality of the affected system. This can result in business disruptions, a flood of calls to your IT help desk, or other impacts.
4. Preserve Evidence. Even if you are not sure if you have a breach, you should still preserve evidence. This evidence can also be used to confirm a breach OR to rule one out. Ruling out a data breach can save you from reputational, legal, and financial risks associated with data breaches. Sometimes you may need to balance the need for evidence preservation against the best next steps to protect your environment. It’s helpful to make this decision in advance of a breach and have a plan. In addition, your response processes may be different depending on your cyber insurance coverage. Contact your insurer immediately if you have breach response coverage, so you can take advantage of critical resources such as breach coaches, experienced incident response firms, and more. You’ll want to discuss your risks and responsibilities with your IR team and your attorneys as you triage the situation and develop your initial response strategy. Be aware that these first steps can happen fast—typically in hours.
5. Patch/Update. Sadly, emergency patches are a double-edged sword. Wait to implement the patch and you risk a breach, implement it immediately and it can damage your network functionality. Sometimes patches are not immediately available, like the Cisco zero day vulnerability we discussed earlier in this blog. This happens quite often. Even when there is a patch, it may not work, or be poorly tested and implementing it can break other network functions. It’s important to decide in advance whether you want to be an early adopter for patches. You should also expect to install multiple patches as the vendor uncovers the extent of the vulnerability. Pro tip: organizations that have a response plan and practice it in tabletop exercises will be the best prepared.
6. Check With Suppliers. Do not assume suppliers will proactively contact you. You should reach out to your suppliers and consider adding breach notification clauses to your supplier contracts. Prioritize your supplier outreach based on which vendors have access to your sensitive data and/or network resources. When you contact your suppliers, ask them to confirm whether they used an affected version of the product or SaaS platform, and if they are actively assessing risk from their supply chain. If you are impacted, get more information so you can determine if they responded appropriately and then evaluate the risk to your organization. You should give them a deadline to share whether they are impacted and tell them to let you know if their answers change.
7. Search your system for Indicators of Compromise (IoCs). How do you determine if an attacker is in your environment? When a zero day vulnerability is reported, the vendor may supply a list of IoCs to help you evaluate your risk from this vulnerability. You can also get IoCs from:
- Security firms/researchers
- Government agencies (i.e., CISA)
- Threat hunting/intel software like Carbon Black
- MISP—open-source threat intel
Popular formats include the Structured Threat Information Expression (STIX) and Yara.
Note that indicators of compromise often change quickly. In the case of the Cisco zero day, researchers were able to track the number of hacked devices around the world using known IoCs—until suddenly all of them disappeared. It turned out that the hackers had changed their strategy so that the known IoCs would no longer work. Quickly, researchers uncovered new IoCs for the adapted malware, and were able to identify hacked devices again.
8. Hunt for Threats. Start by looking for strange activity on the network, then work backwards to find the source. When a zero day exploit is announced, hackers have often already exploited thousands of systems around the world before defenders even know about it. It’s not enough to simply patch and assume you’re good to go. Instead, check and make sure the hackers are out of your environment. Many of the initial payload drops from an attack are just designed to give the attackers a foothold on your systems. By conducting threat hunting in your environment, you can identify and root out any hackers with persistent access, understand the scope of the compromise, and/or prevent a new malware detonation.
We hope you found this update on the Cisco zero day vulnerabilities and our step-by-step zero day attack response checklist helpful! Please contact us if you need support with your penetration testing, advisory, solutions, or training needs. Thanks for reading and check back every week for fresh cybersecurity content!
 Zero Day Attack Response Checklist
Zero Day Attack Response Checklist 