Beyond Passwords: Transitioning to Passwordless Authentication Solutions
 Passwords are one of the biggest headaches in today’s digital world; they are difficult to manage and not very secure. Recently, hackers accessed the personal data of 6.9 million 23andMe users by exploiting reused passwords, compromising details like names, birth years, and DNA information. For millions of people, the exposure of genetic and personal data raises the risk of identity theft, targeted scams, discrimination, and other harm. This is not an isolated case; in fact, 82% of breached organizations say credential misuse or authentication weaknesses was the cause. In good news, passwordless authentication solutions are increasingly available! Let’s explore these solutions as well as the major industry changes in authentication and authentication hacking.
Passwords are one of the biggest headaches in today’s digital world; they are difficult to manage and not very secure. Recently, hackers accessed the personal data of 6.9 million 23andMe users by exploiting reused passwords, compromising details like names, birth years, and DNA information. For millions of people, the exposure of genetic and personal data raises the risk of identity theft, targeted scams, discrimination, and other harm. This is not an isolated case; in fact, 82% of breached organizations say credential misuse or authentication weaknesses was the cause. In good news, passwordless authentication solutions are increasingly available! Let’s explore these solutions as well as the major industry changes in authentication and authentication hacking.
New Voice Cloning Attacks Can Undermine Passwords
When users forget their passwords, what do they do? They call the Help Desk and request a password reset. Unfortunately, criminals are all too familiar with this process, resulting in a recent spate of voice attacks targeting IT help desks. For example, in the recent MGM case, hackers reportedly called the company’s IT service desk and convinced them to reset a user’s password. Okta has warned that attacks against IT service desks are a trend, and that hackers use them to reset MFA on administrator accounts, leading to full takeovers.
Voice cloning is poised to exacerbate these issues—and create more. Already, scammers are using voice cloning tools to commit financial fraud, such as a recent case where an elderly victim paid $17,000 to scammers after they put his “son-in-law” on the phone. In reality, they had cloned the son-in-law’s voice using common tools, and made it sound like he was in trouble. Hackers only need about a minute of audio for a cloning program to create a frighteningly accurate voice clone. Then the criminal can type in any arbitrary message, and it will be immediately generated in the cloned voice.
Soon, voice cloning attacks are likely to shift to the business world, where hackers can use these tools to convince managers to request IT-related changes, bypass multifactor authentication and more. Businesses rely on voice authentication constantly. Got a call from the boss? A colleague? A longtime customer? The sound of the caller’s voice is instinctively part of your authentication process. To make matters worse, CallerID spoofing is all too easy for attackers, meaning you can’t rely on the caller’s number to verify their identity—and even the sound of their voice can be easily faked.
As voice cloning technologies become widespread, make sure to review your caller verification processes, and train all employees—including managers, IT Help Desk staff, and more—to use other methods for authenticating callers, such as MFA apps. Speaking of which…
The Latest MFA Bypass Techniques
Email and text (SMS) authentication are popular Multi-Factor Authentication (MFA) tactics—but easy ones for attackers to bypass. One common tactic is for attackers to create a spoofed web site and then trick users into entering their one-time code into the fake site. Criminals can also employ “SIMjacking” to redirect your text messages to their own device, or simply break into your email to retrieve one-time codes (remember, Business Email Compromise is a leading cause of losses, according to the FBI).
Harder to bypass, but not as secure as a passwordless authentication solution, is Microsoft’s authenticator app with push notifications. Since there is no one-time passcode for attackers to steal, it’s not vulnerable to the same types of phishing attacks. However, attackers have still found ways around it. For example, in “MFA fatigue” attacks, hackers try to trick users into approving pop-up MFA requests by sending repeated MFA app notifications until the victim gets tired and approves the request, allowing the attacker to login.
Microsoft now offers “number matching,” which adds an extra layer of security by requiring the user to type in a number shown on their push notification. This helps prevent users from accidentally approving pop-up MFA requests.
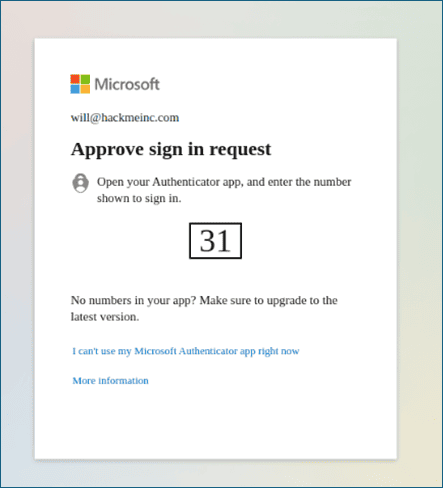
Image: Microsoft number matching screenshot
As you can see, MFA is an arms race and criminals will keep adding tools to bypass or circumvent it—so while authenticator apps are helping now, it’s important for your organization to keep current on best practices as they will continue to change.
The Shift Towards a Passwordless Future
Many large providers are looking to passwordless authentication solutions to enhance security and simplify the user experience. Fortunately, the FIDO Alliance is helping to drive and coordinate the standard technical specifications required for an industry shift to passwordless authentication. These standards also incorporate privacy principles that include ensuring that your personal biometric information stays on your personal device and is not transmitted to reduce your risk of losing biometric data. Technology powerhouses Apple, Google, Microsoft and others have agreed to support the FIDO Standard in order to provide expanded passwordless sign-on, and we’ll share how they are begging to implement these standards a little later in the blog. First, let’s look at how the new FIDO principles work. Here are the steps:
- The online service will prompt you to pick a compliant device.
- FIDO authentication is unlocked with a fingerprint.
- The device creates a new key pair.
- The public key is sent back to the online service (for more information, watch our short video on private and public key encryption or our 1-hour on-demand encryption webinar)
- The private key and info about how you authenticate never leave your device.
Here’s an illustration of the steps from the FIDO alliance:
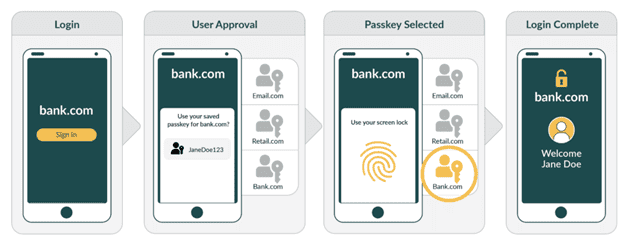
Image courtesy of: https://fidoalliance.org/how-fido-works/
As you can see, the passwordless authentication solution above is simple and more secure. The transition to a more secure passwordless future is already happening, but it will take time for this to roll out to all applications and organizations.
Google, Apple, and Microsoft Move to Stronger Default Authentication & Passwordless Authentication Solutions
Many large organizations are moving to stronger default authentication requirements. For example, Apple has already rolled out a passwordless authentication solution with Apple Passkeys (which are public key cryptography) based on the FIDO and W3C standards. Apple Passkeys replaces passwords by using the key pairs we described above along with biometric authentication to authenticate the user in the app like the FIDO illustration we shared earlier.
In addition to Apple’s passwordless authentication solution, Google has made their Biometrics Passkey systems the default for their passkey security. While you can select an alternative, this passkey is faster than password sign in and it’s much more secure.
Finally, Windows Hello for Business is rising in popularity and offers a fingerprint or facial recognition scan for authentication (although it can also be configured to use a less secure PIN). This technology works for both on-premises resources and cloud applications. However, if your organization uses passwordless authentication solutions you should ensure that you have a plan for lost or stolen devices so you can prevent fraudulent authentication and delete the biometric data to keep your network secure.
What To Do Until Passwordless Authentication is Widely Available
Someday strong, passwordless solutions will be widely available. Until then, businesses need to stay on top of attacker trends and adapt quickly to resist the latest password-related attacks. Here are tips for strengthening your authentication today, while preparing for a passwordless future:
- Choose strong and unique passwords to resist attacks. Make sure users do not reuse passwords in more than one account and choose long passwords (longer passwords are more difficult to break.) Check out our password length blog to find out how long it takes for hackers to break passwords of different lengths.
- Use multifactor authentication (MFA). Any MFA is better than no MFA (and there are still sites and apps out there with no MFA!) If passwordless authentication solutions are not available, authenticator apps and hardware keys like Yubikey are the best bets. You can screen apps to see what kinds of MFA they support using https://2fa.directory/us/. Use this tool to select apps with strong MFA options.
- Use password managers. This enables you to generate and store unique passwords that the manager will remember for you. It is less risky than choosing weak passwords and easier to remember.
- Train your employees to spot phone-based scams like voice cloning and to authenticate requests using a different means of contact—such as calling a known number or a video call to authenticate the user.
- Carefully verify callers. Help desks and call centers should consider caller verification with Okta or Duo. These apps require you to use your app to authenticate the caller. Help desks and call centers are incorporating this verification to avoid social engineering attacks like the one that led to the MGM Resorts breach.
- Conduct cloud configuration reviews. Make sure your cloud apps are configured to securely implement MFA, and to prevent attacks such as MFA fatigue and more. LMG’s team routinely reviews cloud app configurations and checks MFA setups, so contact us if you need help.
- Deploy Single Sign-On (SSO). Use an identity provider like Azure or AWS as the identity provider to establish secure access and then pass that identity back and forth to multiple different applications for streamlined authentication.
- Use Identity and Access Management (IAM) solutions. IAM is a collection of tools and processes used to organize identities, control access permissions, authenticate users for different services, and more.
We hope you found this update on authentication technologies and passwordless authentication solutions helpful! Please contact us if you need help with cloud MFA configuration, voice social engineering training, authentication policies and development, penetration testing, and a wide range of cybersecurity advisory and solutions products. Our experienced team is ready to help!
