Top 10 AWS Security Issues and How to Solve Them
 Cybercriminals are targeting your cloud, and the results are costly. Just last week, Europol arrested a hacker that broke into more than 1,500 cloud accounts and created over 2 million virtual servers in order to mine cryptocurrency—at the victims’ expense. AWS security issues are especially concerning: Amazon Web Services has over 1 million global users and boasts the highest cloud market share at 32% in the third quarter of 2023. Read on for LMG’s list of the top 10 AWS security issues and how to solve them.
Cybercriminals are targeting your cloud, and the results are costly. Just last week, Europol arrested a hacker that broke into more than 1,500 cloud accounts and created over 2 million virtual servers in order to mine cryptocurrency—at the victims’ expense. AWS security issues are especially concerning: Amazon Web Services has over 1 million global users and boasts the highest cloud market share at 32% in the third quarter of 2023. Read on for LMG’s list of the top 10 AWS security issues and how to solve them.
Misconfiguration is Rampant—and Hackers Know It
Source: Qualys TotalCloud Security Insights Report
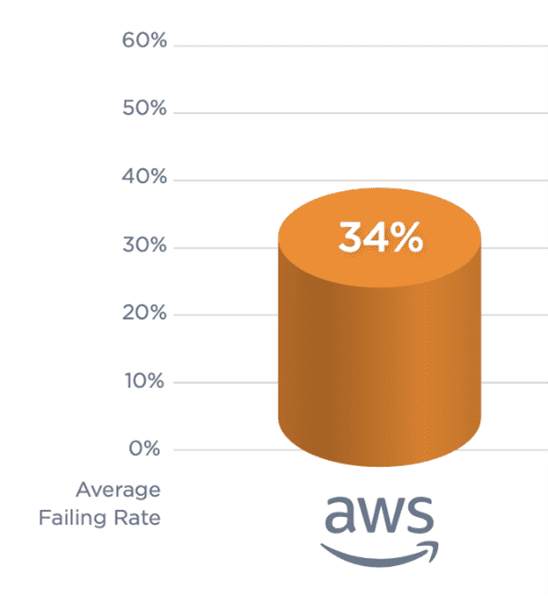
“Cloud default settings are becoming more secure, but there is always room for improvement,” notes Tom Pohl, penetration testing principal consultant. “It’s important that organizations take the time to plan and strategize appropriately.” According to the 2023 Qualys TotalCloud Security Insights report, the average failure rate for AWS security control review is 34%. Cloud environments are complex, and often IT staff do not have time to stay up-to-date with provider default settings and best practices. At the same time, hackers are always finding new ways to exploit common misconfigurations.
Without the proper access controls applied, cybercriminals can easily invade your AWS environment and engage in data theft, exploitation, and extortion. Regular cloud configuration reviews are critical for keeping up with changes in the threat landscape.
Top 10 AWS Security Issues
While AWS is responsible for the security of the cloud itself, the provider emphasizes that organizations are responsible for securing everything within their cloud instance. Dan Featherman, chief product officer at LMG Security, has analyzed the data from our expert team’s AWS Cloud Security Assessment engagements and compiled a list of the top 10 AWS security issues and how to solve them.
The following research highlights critical—and all-too-common—oversights that expose businesses to exploitation and provides proactive guidance on reducing risk. As a guiding principle, our team uses the Center for Internet Security (CIS) Amazon Web Services Benchmarks as a foundation. Now let’s dive into the top 10 AWS security issues:
- Improperly Configured Network Access Control Lists (NACL). Securing your cloud infrastructure is just as important as securing your internal infrastructure. To prevent your organization’s data, resources, and users from being compromised, it is imperative that NACLs and security groups block unrestricted ingress access to remote server administration ports. [See CIS Benchmark 5.1-5.3]
- Multi-Factor Authentication (MFA) Not Enabled
Multi-factor authentication is a critical piece of securing your environment and must be enabled for all users with a console password. In 2023, 82% of organizations that experienced a breach attributed authentication weakness or credential misuse as the cause. Passwords alone are not a good line of defense and are rife with insecurity. When choosing an MFA solution, it is important to choose carefully. Text (SMS) and email authentication are popular options but are highly susceptible to bypass techniques. Instead, opt for a more advanced option such as a hardware keys or an authenticator app with push notifications. For more information on the latest authentication technologies, read our blog on authentication trends and the shift to passwordless authentication. [See CIS Benchmark 1.10] - User Permissions Granted Improperly
Identity and access management (IAM) is amongst the top AWS security issues. According to CrowdStrike’s 2023 Cloud Risk Report, 47% of critical cloud misconfigurations are due to improper identity and access controls. In AWS, IAM policies are used to determine a user’s level of access to data, services, and functions. Though these permissions may be granted by directly editing a user’s policy or directly attaching a policy to a user, the only appropriate method is to add users to groups with defined policies based on principles of least access. Using groups to define and manage policies greatly reduces the risk of users having inappropriate permissions and is a security best-practice. Check out our AWS security best practices checklist for more information. [See CIS Benchmark 1.15] - Improper S3 Bucket Settings
Improperly configured S3 Buckets pose a significant threat to your organization and put you at risk of ransomware attacks. To ensure data security and integrity, S3 Buckets must be configured with “Block public access (bucket settings)”. This setting prevents all S3 Buckets and their contents within your account from becoming publicly accessible. [See CIS Benchmark 2.1.5] - Insecure Passwords
Until passwordless authentication solutions are widely available, it is important that all organizations adopt and implement strong password policies. Adhering to minimum length requirements will greatly reduce the risk that passwords are compromised by brute force attacks. Our expert team strongly recommends that privileged accounts within your organization, such as service accounts and administrators, have a minimum password length requirement of 25 characters. Regular users should adhere to a password length requirement of 16 characters. To help with the security of these accounts, improve policy adoption, and ensure passwords are not reused, we urge organizations to provide all users with a strong password management solution. For more information on password best-practices, please see our recent blog on a data-driven approach to password security. [See CIS Benchmark 1.8] - Improperly Configured S3 Bucket Multi-Factor Authentication
It is not enough to simply implement MFA; it must be configured properly to protect against a multitude of attacks. When considering the security of S3 Buckets, it is imperative that MFA Delete is enabled. For more information on MFA, please see our Multi-Factor Authentication Overview & Best Practices tip sheet. [See CIS Benchmark 2.1.3] - Failure to Implement Appropriate Logging
Cybercriminals are constantly searching for ways to access data. In order to identify malicious access requests, organizations must enable AWS CloudTrail and integrate it with CloudWatch Logs. This ensures that requests are recorded and that they can be monitored in real time. [See CIS Benchmark 3.4] - Access Keys Not Rotated
Access keys contain two components: an access key ID and a secret access key. These access keys must be rotated at least every 90 days to improve your security hygiene. [See CIS Benchmark 1.14] - AWS Security Hub Not Enabled
For visibility into your organization’s overall AWS security, we recommend that organizations enable AWS Security Hub. This tool integrates with many third-party products and gives you the ability to identify issues, analyze security trends, and prioritize the most pressing security problems for your organization. [See CIS Benchmark 4.16] - Lack of MFA Hardware Token Adoption for Root User
The most privileged account in AWS is known as the “Root User”. To ensure the highest level of security for this account, it is strongly recommended to implement the use of a hardware token, rather than the common MFA application. [See CIS Benchmark 1.6]
As cloud adoption grows, so will the number of cybercriminals who attempt to exploit it. Organizations must prioritize the proactive management of cloud-based threats and routinely evaluate their security posture to safeguard their systems and data. Though this may feel daunting, if you need help assessing your AWS security issues our expert team is available to help. Please contact us for more information on cloud security assessments, penetration testing, and other high-impact cybersecurity measures.
