A Real-World Cyber Attack Simulation: How a Hacker Can Breach Your Organization in One Weekend
 The rise of software exploits, particularly zero-day vulnerabilities, has become a potent weapon in the hacker’s arsenal. In this blog, we delve into how attackers use these vulnerabilities to break into organizations in a single weekend! Our Penetration Testing Team Manager Tom Pohl takes us through a cyber attack simulation and provides a breakdown of the tactics today’s attackers are using to breach your organization’s defenses.
The rise of software exploits, particularly zero-day vulnerabilities, has become a potent weapon in the hacker’s arsenal. In this blog, we delve into how attackers use these vulnerabilities to break into organizations in a single weekend! Our Penetration Testing Team Manager Tom Pohl takes us through a cyber attack simulation and provides a breakdown of the tactics today’s attackers are using to breach your organization’s defenses.
More Information is Now Available for Free on the Dark Web
While the dark web has many legitimate uses, it undeniably serves as the largest clearing house of tools and information used by today’s cyber criminals. Criminals can quickly search databases and shop for attack tools, target lists, and more, often for less than the cost of your family dinner at a quick-service restaurant. What’s particularly alarming is the increasing availability of information about these vulnerabilities and exploits in free listings, forums, and databases—making them accessible to a broader range of people and criminals. Why is this such a big problem? Microsoft found that on average, it takes only 14 days for an exploit to be “available in the wild” (this means information is readily available for attackers), but it can take up to 120 days for the exploit to be incorporated into vulnerability scanning software. However, AI is rapidly increasing how quickly attackers can create an exploit, and our LMG Security team and many others are starting to see some vulnerabilities exploited just hours after they are publicly reported. Let’s take a look at a classic, real-world pentesting cyber attack simulation to discover how an attacker can take over your network in a single weekend using a simple zero-day vulnerability.
A Real-World Pentesting Cyber Attack Simulation
As we mentioned above, a lot of exploit information is readily available for free. In this cyber attack simulation, our Penetration Testing Team Manager Tom Pohl was watching the news and got the tip he needed to launch a successful penetration testing attack! Let’s break down how the attack happened.
- Scanning for a target. Tom decided to check if his penetration testing target was using F5’s BIG-IP software that contained a newly discovered vulnerability that he heard about in the news. This is a very targeted example; in general many hackers will simply scan the internet looking for vulnerable organizations. Tom was happy to discover that his target used F5’s BIG-IP software and its web management interface was exposed to the internet. Why did Tom choose a new vulnerability for this cyber attack simulation? In this case, the new F5 vulnerability was not yet incorporated into vulnerability scanning software—so using this new vulnerability increased Tom’s likelihood of breaking into a large array of targets. In this particular vulnerability, F5’s misconfiguration of placing the management interface on the internet became the entry point for Tom’s attack.
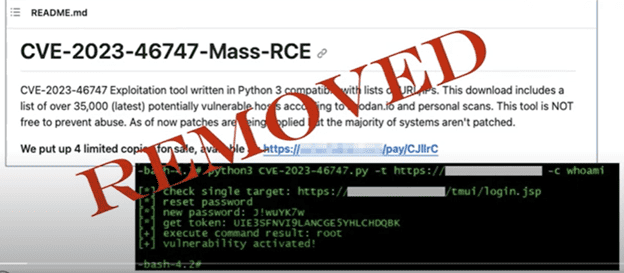
- Finding a proof of concept. Tom’s next step was to try to find a proof of concept on GitHub. This is often an early step for attackers. Tom actively searched for an exploit for the new F5 vulnerability and found an ad for a full script that had recently been taken down. He kept searching and found a partial broken script someone was writing to leverage this exploit and he was able to fix it, modify it, and create a working exploit.
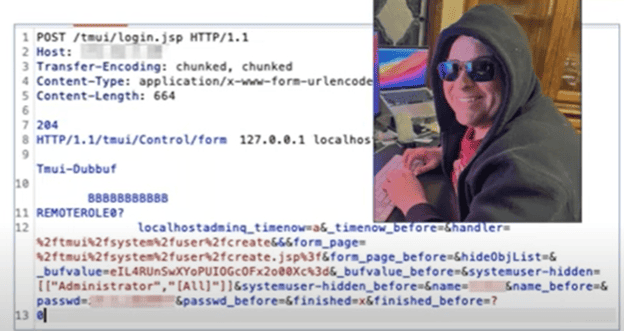
- Exploiting the Vulnerability: Using the exploit, Tom performed an HTTP smuggling attack by sending AJP (Apache Jserv Protocol) messages directly to the underlying application server container to create an administrator account. He did this by using a penetration testing tool, Burp Suite, to help create the HTTP smuggling attack (where you take one HTTP request and smash another one after it) so F5 would process both and Tom could manipulate the web requests to create a new username and password with administrator-level access.
- Gaining Access: After creating the administrator account, Tom logged in, changed the password, and obtained a token. This small piece of data is like a hall pass and tells the program that Tom is already authenticated! With the token, F5 lets Tom access F5’s API endpoints and execute commands, so he could eventually create a reverse shell, which provided Tom with a backdoor remote access that he can use anytime he wants.
As you can see, it did not take Tom long to use a newly discovered vulnerability to gain full access to his target’s environment. So, what can you do to help prevent attacks like this one in our cyber attack simulation?
The Top 10 Strategies to Protect Your Organization
- Attack Surface Monitoring: Regularly scan and monitor your organization’s attack surface, focusing on internet-facing assets. Identify vulnerabilities that may be exploited, especially in exposed management interfaces. Continuous attack surface monitoring is crucial as vulnerabilities evolve and hackers actively search for targets.
- Conduct Penetration Testing: Schedule an annual human-led penetration test to uncover vulnerabilities that automated tools might miss. This includes actively searching for exploits, like Tom did in our cyber attack simulation. His discovery of the vulnerability in F5’s BIG-IP let him take over a network in just a weekend, illustrating how easily attackers can exploit weaknesses in your network.
- Monitor Threat Intelligence: Stay informed about the latest threat intelligence, especially regarding vulnerabilities affecting your software and systems. Tom learned about the F5 vulnerability through a news article. There are many different free and paid threat intelligence options including the CISA Known Exploited Vulnerabilities Catalog, our favorite free resource.
- Respond Quickly: Swiftly respond to identified vulnerabilities by patching systems or implementing mitigation and containment measures.
- Maintain an Accurate Data Inventory: Maintain an up-to-date inventory of your data and systems. Knowing what assets you have helps your team quickly identify potential security gaps when zero-day vulnerabilities are announced. Tom’s cyber attack simulation demonstrates the risks associated with internet-exposed management interfaces, as well as the risks posed by zero-day attacks. Read our guide to zero day attack response for more information on responding to zero-day threats.
- Segment Your Network: Implement network segmentation to limit lateral movement in the event of a breach. By segmenting the network, attackers are restricted in their ability to pivot from one compromised system to another, minimizing the overall impact of a security incident. Read our blog post on network segmentation best practices for more information.
- Implement the Principle of Least Privilege: Adopt the principle of least privilege, restricting user access to the minimum necessary for their roles. This reduces the potential impact of compromised accounts. Tom’s cyber attack simulation involved creating an administrator account which provided broader access to the environment and showcasing the risks of excessive permissions.
- Deploy Detection Strategies: Implement effective detection strategies, including intrusion detection systems. There are many options, and we can’t cover them all in this blog. Timely detection can prevent further exploitation, if you’re not sure if you have the most crucial detection strategies in place, try our security fundamentals assessment for an expert review of your systems and advice on the best next steps.
- Use Multifactor Authentication: Enhance authentication security by implementing multifactor authentication. This adds an extra layer of protection, even if credentials are compromised. MFA is changing, and going passwordless! Check out our on-demand webinar for all the details.
- Conduct Cloud Configuration Reviews: For organizations using cloud services, conduct cloud configuration reviews. Misconfigured cloud services are a common entry point for attackers and can cause a data breach. An annual cloud configuration review is an easy way to reduce your risk of a breach.
We hope you found this overview of a cyber attack simulation helpful. Cyberattacks are constantly evolving and staying ahead of attackers requires a multifaceted approach to cybersecurity. We could never cover everything in one blog, so read our weekly blog for insights on how to keep your organization safe! Please contact us if you need help with penetration testing, advisory services, cybersecurity solutions, or training. Our expert team is ready to help!
NOTE: Exploiting vulnerabilities without authorization is a crime, and you should never do it. When we perform pentests, we have contractual permission from the client for testing and exploiting vulnerabilities during our engagement.
