The 4 Top Cybersecurity Threats of 2022

Our Predictions for the 4 Top Cybersecurity Threats of 2022
- Zero-day exploits and mass vulnerability abuse
- Cross cloud attacks
- Exposure extortion
- Supply chain attacks
Let’s dive right in; there’s a lot of ground to cover!
Threat #1: Zero-Day Exploits and Mass Vulnerability Abuse
Hackers are leveraging flaws in commonly used software to compromise endpoints around the world. Today, digital information and applications are critical for almost every aspect of business operations. In 2021, the average number of SaaS applications each organization uses has risen to a staggering 110 apps. If hackers uncover a vulnerability in any of your organization’s software or SaaS apps, you can be targeted with a zero-day exploit or mass vulnerability attack.
How will criminals leverage these vulnerabilities? Commonly, they will use these zero-day exploits and mass vulnerabilities to infiltrate your environment and install malware, steal data and credentials, move laterally to expand their reach and privilege, and to execute commands.
With the increasing number of code libraries and software complexity, mass vulnerability abuse was rampant in 2021 and is bound to continue in 2022. Some of the most widely hacked software products in the last year included Microsoft Exchange, Atlassian Confluence (a widely used piece of Enterprise Collaboration software), Windows 10 and the Log4j package. While it’s easy to see how the Exchange and Windows 10 exploits can impact thousands of organizations, let’s look at how the lesser-known Log4j exploit can affect risk around the world.
The Log4j exploit can reach so many organizations because it is part of the widely used Apache Log4j Java-based logging library. A staggering number of users utilize this code in their software and SaaS applications. Organizations such as SAP, Apple, Tesla, VM Ware, Cisco and many, many others had to scramble to quickly patch their internal software and roll out patches to fix vulnerabilities in their products. Checkpoint found that there were over 60 mutations of the Log4Shell exploit in less than 24 hours and over 1.8 million attempts to exploit this vulnerability in the first few days following its announcement. It’s clear to see why mass exploits will continue to be one of the top cybersecurity threats in 2022.
How can you reduce your risk of an attack?
- Ask your software vendors for a Software Bill of Materials (SBOM). What is a Software Bill of Materials (SBOM)? It is an inventory of all software components and code bases, which can include: open-source software, dependencies, packages, vendor agents, SDKs, APIs, and more that are used in a software program. Having this information ensures you know what’s in your environment, and it will help you respond quickly in the event of a mass exploit like Log4j. The Colonial Pipeline attack is part of the reason the Biden Administration created a 2021 Executive Order that now requires federal agencies to get SBOMs from vendors. We predict SBOM requests will increase in 2022, and it’s smart to make this a requirement for your new vendors.
- Subscribe to exploit intelligence services and keep an eye on cybersecurity news. It’s important that you act quickly when mass exploits are announced. Many companies and organizations have cybersecurity alert lists or publish this information in their newsletters. You can sign-up for our alerts and newsletter list, use another company, or just watch the cybersecurity news sites for mass exploit alerts.
- Stronger software patch management policies. According to a survey conducted by the Ponemon Institute, 42% of the respondents that had been breached stated that the cause was a known, unpatched vulnerability for which a patch was available but not applied. Many organizations have a patch management policy that calls for monthly or bimonthly patching cycles. But when a critical vulnerability is announced, hackers may actively try to exploit your server within hours or days, not weeks. You need to update your patch management policies and procedures to ensure quicker patching for critical vulnerabilities and ensure strong patch verification. Many organizations think they have successfully patched their software, only to find out later the patch failed. Consider using Microsoft WSUS or a commercial patch management system, and always verify your patches. If you need help optimizing your software patch management program, read our recent blog on software patch management tips.
- Enhance your monitoring and logging policies. Ensure that logging is turned on and set appropriate retention rates. Consider centralizing your logging with SPLUNK or Elkstack/Kibana. Then make sure you are monitoring your logs. For tips, watch our video on monitoring and logging.
- Proactive threat hunting. This is becoming one of CISA’s top recommendations for first steps to take when a zero-day exploit or mass vulnerability is announced. Hunting for unusual activity enables you to see if an attacker is lurking in your environment. Since many zero-day exploits can bypass antivirus, if you don’t have a threat hunting program or tools in place, you should. Read our blog on threat hunting for more information or you can outsource threat hunting.
- Get a risk assessment. A cybersecurity risk assessment involves identifying what you need to protect (i.e., sensitive data, critical systems) and the vulnerabilities and potential threats associated with those assets. Your vulnerabilities and threats are then assessed for likelihood and potential impact of an exploit, taking into account existing security controls (technical or non-technical) that may mitigate or lower the overall likelihood or impact of an exploit. Read our blog on how to get the most out of your risk assessment.
Threat #2: Cross-cloud compromise
As organizations continue to grow their cloud portfolios, share credentials, and build trust relationships between platforms, criminals will increase their focus on cross-cloud compromise, meaning that they leverage access to one cloud application and spread to others. Not familiar with cross-cloud compromise? Let’s look at an example of a recent case. One recent attack began when a finance clerk fell victim to a phishing attack. This gave the criminal access to the clerk’s email password and the criminal was able to easily access the clerk’s email account, since it did not require multi-factor authentication. The criminal looked through the clerk’s emails and identified the organization’s payroll vendor. The criminal then entered the clerk’s email password into the payroll login screen (sadly, the clerk used the same password for multiple accounts) and successfully accessed the company’s payroll cloud platform. The lucky criminal used the access to redirect the direct deposits of multiple employees into the criminal’s bank account—which the criminal emptied and closed after the next pay period.
How can your organization avoid a cross-cloud attack?
- Use multi-factor authentication (MFA):MFA is an added layer of protection to verify it’s really you who is accessing your account and not a hacker. This is one of the simplest things an organization can do to reduce risk in a variety of areas. Most MFA programs ask for two out of three of the following factors:
- Something you know – such as a username or password
- Something you have – a physical token or authenticator app for example
- Something you are – such as a fingerprint or retinal scan
An attacker will likely have only one of these factors, such as a password. The extra MFA factor is a simple way to keep hackers out of your account. Enable MFA on every internet-facing account and device possible. You should also consider stronger alternatives for authentication that don’t rely on static secrets. Many organizations now use authenticator apps, issue hardware fobs such as the Yubikey for authenticating employees, or set up biometric authentication using fingerprints or facial recognition. But any type of MFA is better than no MFA.
- Implement a password manager. Humans can only remember so much information. A good password manager suggests and securely stores each password in an encrypted vault; this ensures your team members won’t need to re-use passwords and the suggested passwords are usually stronger than what most people create. When selecting a password manager program for your organization ensure it uses MFA, and train team members to use a strong master password to protect their vault. See our password cheat sheet for easy tips on login security.
- Provide regular cybersecurity training for everyone in your organization. As we mentioned in the cross-cloud attack case above, phishing was the root cause of the breach. The most common cause of a data breach is human error. According to the 2021 Verizon Data Breach Investigations Report (VDBIR), social engineering and phishing accounted for over 80% of the successful attacks. Every person in your organization should have general cybersecurity training, advanced training for IT teams in breach response, and executive cybersecurity risk training. Whether you subscribe to a security awareness training portal with built-in phishing tests, provide monthly cybersecurity tips and articles to your employees, or do a quarterly training – however you can afford to start, you should start if you haven’t already. In fact, you can download free tip sheets that you can email directly to your employees about phishing prevention, password security and remote work safety and get started right now!
- If you notice signs of suspicious activity, consider quickly implementing a FULL password reset, including the user’s email. When facing this type of compromise, many IT teams make the mistake of only resetting the password for a specific cloud account. All too often, criminals start by hacking email or a local system, and spread to the cloud. If the criminal is still lurking in the employee’s email account they can simply reset whatever passwords you change and strike again! When in doubt, always reset the victim’s email password, as well as any other passwords that may be related.
Threat #3: Exposure Extortion
Exposure extortion is ransomware’s equally evil cousin, and these two tactics were commonly used together in 2021. However, we’re seeing a trend that some criminals are not bothering with ransomware (which is a lot more work) and are just focusing on exposure extortion. In exposure extortion attacks, criminals are stealing the data, sometimes shopping it around to competitors, pressuring victims to pay by informing their customers and partners that their data will be exposed if the organization doesn’t pay, and then exposing the data on a data leak site or selling it on a Dark Web marketplace.
The graphic below shows how an extortion exposure attack works.
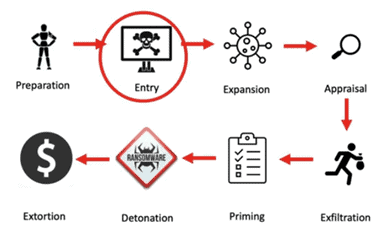
It’s easier than ever for criminals to conduct extortion attacks, especially if they partner with a third-party extortion service and data leak site. Exposure extortion has much lower start-up costs compared with ransomware since there is no need to develop or buy malware. All the criminal has to do is hack into an organization and steal data. After that, a third-party extortion service can take care of most of the extortion infrastructure and processes. Ransomware gangs like Conti provide playbooks with strategies that help the criminals to evade detection, dwell in the environment longer, identify the best types of data to steal, and learn how to leverage normal IT tools to expand their reach farther, faster, and more efficiently. This enables criminals to steal more sensitive data and yields a bigger payout for both parties.
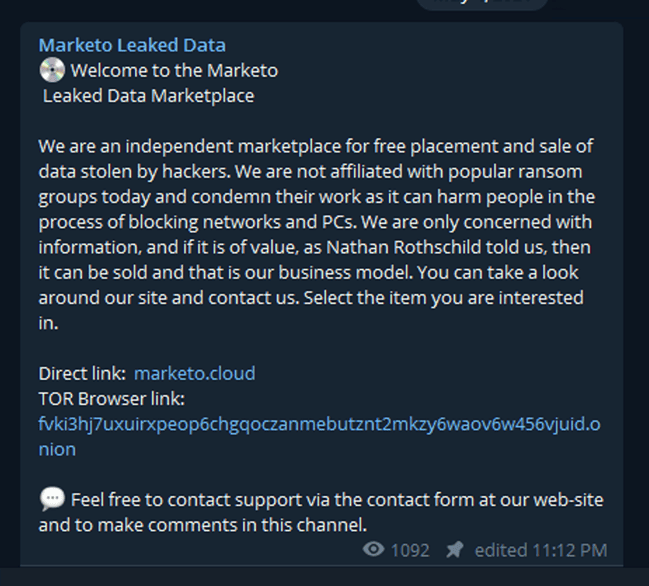
In the image below, you can see a screen shot of the Marketo Leaked Data Marketplace—a third-party extortion services supplier. In the image below you can see Marketo claims extortion is a kinder, safer alternative to ransomware.
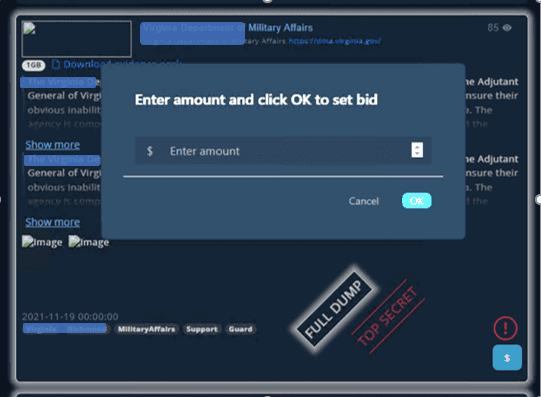
In the next image below, you can see Marketo offers its criminal customers a convenient marketplace and facilitates the auction of the data if the victim does not pay.
How can you reduce your risk of exposure extortion? You’ll want to start with the tips we’ve outlined in the mass vulnerabilities/zero-day exploits section of this top cybersecurity threats blog–these tips apply here too! In addition, you should also:
- Implement strong data loss prevention (DLP) policies and solutions. You can get affordable DLP software that supports cloud and on-premises data, offers real-time data analysis, and covers the data lifecycle, regardless of whether the data is at rest, in transit or in use.
- Minimize the data you retain. Data is hazardous material. Data loss can create legal and regulatory issues and harm your organization’s reputation. Inventory your data and assets to determine what data you have, where it is stored, your retention policies, who has access, and whether it is encrypted at rest. Then, decide what data you really need, and get rid of what you don’t need. Reducing your data reduces your risks.
Risk #4: Technology Supply Chain Attacks
Attackers take advantage of technology suppliers in order to compromise hundreds or even thousands of organizations quickly. Recent cases include the Shutterfly attack by Conti, the Kronos workforce management platform hack (customers are already suing Kronos for the service disruption and ripple effects), and the Netgain healthcare service provider hack (healthcare organizations are still announcing breaches over a year later). In some cases, the criminals hack a service provider and expand laterally into connected environments or install malware in a product which is distributed far and wide. In other cases, they hack into a cloud service and steal hosted customer data. Regardless of the precise model, technology supply chain attacks were big in 2021 and will continue to be one of the top cybersecurity threats in 2022.
The consequences from supplier exploits just increased with the FTC’s recent warning that organizations MUST take reasonable steps to secure customer data from Log4j and other known vulnerabilities or face potential legal action. In today’s digital world where every organization uses myriad software programs, web apps, and cloud platforms—and may even directly integrate with partners’ systems—technology suppliers are a crucial part of every organization’s cybersecurity. Here are some strategies to reduce your risk of falling victim to one of the top cybersecurity threats of 2021 and 2022:
- Conduct an inventory of technology suppliers, including service providers, cloud vendors and software products. You can’t secure your environment until you understand your exposure.
- Limit access. You can cut down on your work and your supply chain cybersecurity risks by limiting suppliers’ access to your IT resources and sensitive data. Often, suppliers have more access than they really need and consequently pose more risk to your organization than necessary. Conduct a review of supplier access at least annually, and limit access to the minimum necessary for them to get the job done.
- Establish clear, documented standards for your own organization and your suppliers. Common frameworks such as ISO27001 or the NIST Cybersecurity Framework are excellent starting points for establishing baseline standards. You can also download this supply chain security checklist for additional program tips.
- Delegate cybersecurity requirements to vendors in your contracts to ensure mutual understanding and commitment. Also, when necessary, document requests for improvements and set a deadline. Make it a contractual requirement that ALL your vendors and partners provide you with timely notice if they are impacted by a breach or a major exploit.
- Vet your vendors routinely, both during the new vendor selection process and at regular intervals. Ask your suppliers/prospective suppliers about their security and ensure that they meet your standards.
- Ensure that your suppliers are actively vetting their supply chain (fourth- and even fifth- party risks are real and have led to many data breaches and cybersecurity incidents). The NIST Cybersecurity Framework includes a subsection for supply chain risk management (ID.SC); suppliers that use this as their controls framework will have a foundation for implementing their own vetting programs.
- Involve key suppliers in your response planning. Establish a strong understanding of the cybersecurity processes for each of your key suppliers and create joint action plans in case of an exploit or incident. This process can identify and close potential gaps, as well as provide a framework that speeds response in case there is an incident (you could even involve them in your tabletop incident response exercises).
- Get vendor buy-in on standard software vulnerability management processes, such as critical software patches. As criminals target supply chain cybersecurity weaknesses, limit your exposure with a strong patch and update management program. Quickly applying security updates can decrease your risk of supply chain software breaches.
For more information on supply chain attacks and detailed recommendation for vetting your suppliers, read this supply chain security blog.
Tackling the Top Cybersecurity Threats of 2022
The cyber threat landscape is changing. Every organization needs to continuously adapt to the changing threat landscape to ensure you are prepared. Effective risk management strategies will help keep you ahead of the cybercriminals!
If you need assistance quickly and effectively tackling these high-priority items, contact LMG’s team of experts today. Whether it is testing, training, consulting services to help you refine your policies and programs, or incident response, our expert team is ready to help.
