How to Reduce Web App and Cloud Application Security Risks
 It’s no secret that organizations rely on cloud storage as well as web and cloud applications as an affordable way to connect today’s geographically dispersed internal teams, partners, and suppliers. “There is no business strategy without a cloud strategy,” said Milind Govekar, vice president at Gartner. Garner predicts that by 2025, 95% of new digital workloads will be deployed on cloud-native platforms. Hackers are aware of this trend and have increased their focus on cloud and web app attacks accordingly. In fact, a new survey found that 39% of businesses experienced a cloud data breach last year and for the second year in a row, the 2023 Verizon Data Breach Investigations Report found that web apps were the top initial action vectors in a data breach. Clearly web app security and cloud application security should be a priority. Let’s dive into some simple ways you can reduce your risk.
It’s no secret that organizations rely on cloud storage as well as web and cloud applications as an affordable way to connect today’s geographically dispersed internal teams, partners, and suppliers. “There is no business strategy without a cloud strategy,” said Milind Govekar, vice president at Gartner. Garner predicts that by 2025, 95% of new digital workloads will be deployed on cloud-native platforms. Hackers are aware of this trend and have increased their focus on cloud and web app attacks accordingly. In fact, a new survey found that 39% of businesses experienced a cloud data breach last year and for the second year in a row, the 2023 Verizon Data Breach Investigations Report found that web apps were the top initial action vectors in a data breach. Clearly web app security and cloud application security should be a priority. Let’s dive into some simple ways you can reduce your risk.
Web App Security and Cloud Application Security Go Together Like Peanut Butter and Jelly
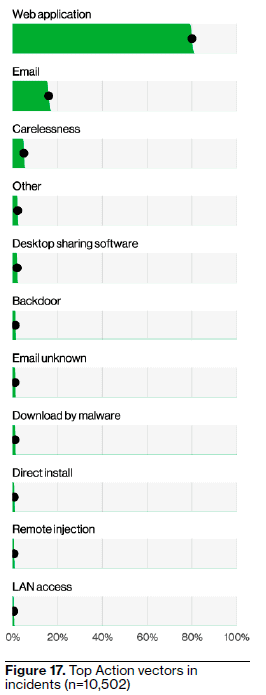
Source: 2023 Verizon Data Breach Investigations Report
Why are we tackling both web app and cloud application security in one blog? Web app and cloud application security are closely related because web applications are both often hosted and operated within cloud environments. This creates a symbiotic relationship where the security of one significantly impacts the security of the other, plus there’s a lot of overlap in the security recommendations to reduce your risk from both web app and cloud application security. What are the top three things they have in common?
- Hosting Environment. Many modern web applications are hosted in cloud environments, whether it’s on public clouds like AWS, Azure, or Google Cloud, or private clouds. Web and cloud applications rely on these cloud environments to provide the infrastructure and resources they need to run.
- Shared Responsibility Model. The cloud provider is responsible for the security OF the cloud, while the customer is responsible for their security IN the cloud. It is up to the customer to properly utilize and configure the security features that a provider makes available.
- Data Storage. Web applications often store and process sensitive user data. This data is typically stored in databases hosted within the cloud. Securing access to this data is crucial for both web app and cloud security.
How are Web and Cloud Applications Breached?
Web and cloud applications are frequently breached using:
- Injection attacks – including SQL injection and cross site scripting
- Broken and/or weak authentication
- Server misconfigurations
- API security issues
- Vulnerable components such as open-source libraries containing compromised code and zero-day vulnerabilities
Let’s look at a couple of examples. In what is shaping up to be one of the biggest cloud attacks of the year, the MOVEit attack impacted both on premises and cloud applications using an injection attack. Designed to be a secure, high-volume file transfer solution between organizations and customers, a zero-day breach of the MOVEit cloud and on premises applications resulted in staggering amounts of data exfiltration. This breach is estimated to have impacted more than 600 organizations, 40 million individuals and cost over $6.5 billion to date—and new reports are ongoing.
But let’s not leave out web app security breaches. One of the most infamous web app breaches, and a prime example of the dangers of misconfigurations, was what was commonly dubbed the F12 Missouri breach. The Missouri Department of Elementary and Secondary Education (DESE) published a web application that enabled easy sorting of public information. An unfortunate misconfiguration enabled too much data to be pulled into the app and caused the accidental exposure of more than 100,000 teachers’ social security numbers. The painful part of the misconfiguration was that all it took was one reporter pushing the F12 key to see all of this superfluous, sensitive data that was accidentally pulled into the web app. In a stunning turn of events, the Missouri Governor then accused the reporter of hacking, resulting in the FBI generating a report detailing that stumbling across information from a misconfiguration and properly reporting it did not qualify as hacking.
How is Cloud Data Protected?
Cloud data is generally protected in three ways:
- Authentication. This step verifies the identity of the user, ensuring that they are who they claim to be.
- Authorization (IAM – Identity and Access Management). IAM limits access permissions and confirms whether the user should have access to specific resources or data.
- Encryption. Data is transformed into an unreadable format, and only individuals with the authorized decryption key can decipher it. This ensures that even if unauthorized access occurs, the data remains secure and confidential.
Let’s look at how this is commonly used in practice. Cloud application security solutions use access tokens that tell systems that a user has already authenticated. This is designed to increase speed and productivity since you don’t need to use your username and password each time you access the system. In addition, these authentications expire after a set period of time. This simplifies and speeds logins and lowers employee frustration which helps prevent users from trying to find workarounds. Tokens are a middle ground designed to help balance usability/productivity and security, but are by no means perfect. How do hackers commonly breach this credential? If a user clicks on a phishing email the hacker can steal these authentication tokens to bypass Multi-Factor Authentication and cause a cloud compromise.
How Do You Protect Your Organization if Your Cloud Provider Gets Hacked?
- Use long, unique passwords and a password manager. Change your password regularly and immediately if you think it has been compromised.
- Conduct an asset inventory. Know where your data is stored and use IAM to limit access to it. If there is an attack on your cloud provider, this can reduce access to your data.
- Reduce your data. If you don’t need the data, get rid of it! Extra data increases your risk.
- Implement Data Loss Prevention (DLP) controls. This will help you realize if sensitive info is being sent outside your organization.
- Use email encryption. This provides you with your own unique encryption key for your computer. If someone breaks into the cloud version of your app but does not have your encryption key, they can’t break into your email. This is a huge risk reduction technique since it helps prevent further credential theft and MFA bypass attacks.
- Add conditional access policies and impossible travel alerts. This provides notifications that can alert you if something odd is happening.
- Employ enhanced monitoring and logging. Periodically check that user activity is not deviating from what would normally be observed.
The Top 3 Web App Security and Cloud Application Security Best Practices
The top three ways to reduce your web app security and cloud application security risks are:
- Cloud and web app pentesting. We have done numerous web app pentests where clients have paid for expensive outside development they were assured was secure. Following best practices, these customers engaged us for a web app pentest prior to launch and were shocked to discover multiple security flaws that did not show up on the app developers automated security scans. Unfortunately, app development code has a high likelihood of errors. On average, programmers make “about 15 – 50 errors per 1000 lines of delivered code,” and automated scans tend to miss multi-step vulnerability chains that can leave your data vulnerable to criminals. Web app pentests can also find vulnerable open-source library code like the epic Log4J vulnerability that can leave you open to supply chain code breaches. For more details read our blog on the benefits of web app pentesting and how to get the most from your pentest. As we covered in the first paragraph, cloud security gaps and misconfigurations are also a common cause of a breach. Have your cloud configuration checked periodically and include your cloud environments in your annual pentests to ensure you don’t have any security gaps.
- Use good cyber hygiene and security controls.
- Use IAM to limit employee access to only the information each user needs to do their job. This limits access to sensitive data.
- Conduct a data inventory. Have an up-to-date list of what you need to protect and its location. Consider where your sensitive data such as personal, financial, health, passwords, API keys, and network maps are stored so you can limit access to it. Remember to check which software, network drives and appliances, cloud environments, and SaaS programs have access to this information.
- Have current backups. These backups need to include both your on premises and cloud data and they need to be tested regularly.
- Provide employee cybersecurity awareness training. Most attacks involve the human element. It’s common for a data breach to start with phishing or smishing attacks. Providing employee cybersecurity awareness training can turn your employees from a security weak spot to your first line of defense. In fact, IBM’s research says organizations can reduce data breach costs by almost $250K if they implement good cybersecurity awareness training.
We hope you have found this information on web app security and cloud application security helpful! Please contact our team if you have any questions or if you need support. Stay safe!
