Web App Pentesting: A 7-Step Checklist for Uncovering Hidden Vulnerabilities
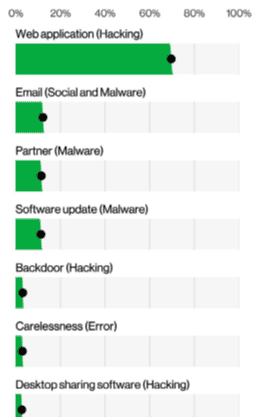
Figure 1: Top Action Vectors in Incidents chart from 2022 Verizon Data Breach Investigations Report
Web applications have transformed the way we conduct business, communicate, and interact with each other—but with this convenience comes risk. All too often, applications contain hidden vulnerabilities, which attackers can exploit to steal sensitive data, capture passwords, or worm their way into your network. The security of web applications degrades over time, as new vulnerabilities such as Log4j are uncovered, so web app pentesting is now a foundational security practice for organizations to identify and mitigate vulnerabilities in SaaS platforms and web applications before the hackers find them.
How big is the problem? Web application hacking was the top action vector that led up to an incident, according to the 2022 Verizon Data Breach Investigations Report. The best way to counter this threat is by regularly enlisting the help of expert testers to identify exploitable vulnerabilities that automated scanners may miss.
But what should you expect from web application pentesting and how do you get the most value for your dollar? Read on for real-world case studies and our web app pentesting checklist.
Understand Your Goals for Web App Pentesting
On average, programmers make “about 15 – 50 errors per 1000 lines of delivered code.” Whether you are deploying a web app for your own internal use, or offering a platform for customers or third parties, it’s crucial to conduct web app pentesting prior to deployment and at regular intervals. Here are 4 goals of web app pentesting:
- Identify and Mitigate Vulnerabilities. Even the best development team leaves vulnerabilities behind—and the results can be devastating if you don’t have a process for finding them. For example, one company recently acquired a web application product and hired LMG’s penetration testing team to conduct web app pentesting. The prior owners assumed that the application was secure. From the Internet, LMG’s team of ethical hackers identified a feature in the web application that allowed users to upload files. Our team specially crafted the filenames so that they contained commands and discovered that when we uploaded the files, we could inject our own commands into the server. “Once we had low-level access to the server, our hackers discovered it was missing a critical patch,” said LMG’s pentest team manager Tom Pohl. “We took advantage of this and escalated to administrator privileges on the system.” A hacker that exploited this vulnerability could have completely taken over the system. Fortunately, this vulnerability was uncovered during testing before hackers found it!
- Meet Compliance Requirements. Regulators are starting to hold organizations accountable for vulnerability management. In a landmark case, the SEC fined First American Financial Corporation $487,616 after a web application vulnerability led to the exposure of over 800 million sensitive title and escrow documents. Organizations that handle sensitive data, such as financial or healthcare information, are often required to comply with industry regulations and standards. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires regular penetration testing of web applications that handle credit card data. Regular web app pentesting helps organizations meet compliance requirements and avoid costly fines and legal action.
- Protect Your Reputation. A data breach can be devastating to an organization’s reputation. News of a breach can spread quickly, causing customers to lose trust in the company and take their business somewhere less risky. The Equifax data breach is an example of the critical importance of web application penetration testing. Equifax is a credit reporting agency that collects and stores sensitive financial information on millions of individuals and businesses worldwide. In 2017, Equifax suffered a massive data breach that compromised the personal information of approximately 147 million Americans. The breach was caused by a vulnerability in the web application software used by Equifax. Although the vulnerability was widely known and a patch was available, a Congressional investigation found that Equifax’s team did not apply the patch in a timely manner, “leaving its systems and data exposed.” As a result, attackers exploited the system and stole massive volumes of data, placing millions of Americans at risk and leaving Equifax’s reputation in shambles. The Equifax case illustrates the importance of a regular web app pentesting and vulnerability management routine. Even if you test a web application extensively upon deployment, new vulnerabilities regularly emerge. To reduce your risk, we advise conducting web app pentesting at routine intervals, along with continuous vulnerability scanning between tests.
- Reduce Costs. The cost of a data breach can be significant, with companies often facing financial losses, legal action, and regulatory fines. Web app pentesting can help reduce these costs by identifying vulnerabilities before they are exploited by attackers. Addressing vulnerabilities proactively can help prevent data breaches, system downtime, and financial losses. This can help organizations avoid the high costs associated with responding to a security incident.
Checklist for Getting the Most from Web App Pentesting
How do you get the most bang for your buck when conducting web app pentesting? Here is a handy checklist:
- Define the scope of the test: Determine the web applications that will be tested, the systems they interact with, and any other relevant factors. Web apps often connect to back-end databases and other apps, so make sure you outline the full scope of access so there are no surprises during the test.
- Set up the testing environment: Create a testing environment that is similar to the production environment to ensure accurate results. Whenever possible, it’s best not to test your production systems, so that your ethical hackers can conduct tests that may impact availability. If you must test in a production environment, make sure your pentest team understands your boundaries and tries to conduct tests during lower-volume timeframes.
- Select your testing methodology: Choose the testing methodology that will be used, such as black-box testing or white-box testing, depending on the organization’s needs. Although web app pentesting can be done as a “black box” test, meaning your ethical hackers start with zero information, it’s usually more valuable to give testers different levels of account access so they can check (for example) what hackers could do if they had access to a normal user account.
- Launch the test: Your ethical hacking team will typically start by gathering information about the web application, such as its structure, functionalities, and technologies used. Then, they will identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and weak authentication using various testing tools. Manual examination is a key component of any high-quality web application penetration test; ensure that your ethical hackers review your application manually and verify the vulnerabilities found during testing to ensure that they are not false positives. Finally, your ethical hackers will attempt to exploit the identified vulnerabilities to understand their impact and severity.
- Reporting: Following testing, your ethical hackers will deliver a report documenting the vulnerabilities found during testing, including their severity, impact, and recommendations for remediation. In addition, your developers may find it helpful to ask for a copy of any raw vulnerability scans conducted during the test. If you are conducting testing on a web application that is already in production, make sure you have clear guidelines for your pen testers, so they know to notify you quickly if they discover a major vulnerability that needs to be addressed right away.
- Remediate vulnerabilities: Take action to remediate the vulnerabilities identified during testing, such as patching the software, improving access controls, or updating configurations. Make sure you truly consider and address the root cause of any issues, such as gaps in development or patch management processes.
- Retest: Perform follow-up testing to ensure that the vulnerabilities have been properly remediated and that the web application is secure. Typically, your pen testing company can issue you an updated report or letter of attestation which documents that issues have been addressed. This documentation may be helpful for customers, regulators, or any other third parties concerned about your web application security.
Your Next Steps
Web app pentesting is a critical component of any organization’s security program. It helps identify vulnerabilities that could be exploited by attackers, meet regulatory compliance requirements, protect your reputation, and keep costs down. You can also check out this blog for answers to frequently asked questions about web app pentesting. By conducting regular web app pentesting, organizations can ensure that their web applications are secure and protected against potential threats.
Need help conducting a web app penetration test? Contact LMG’s team of expert ethical hackers.

