Cryptography 101: Demystifying Cryptography and Cryptocurrency & the Impacts on Cybersecurity
 In today’s digital age, where sensitive information is constantly being transmitted and stored electronically, secure communications and transactions are a foundation of digital banking, commerce, supply chains, and many other services that we use in our personal and professional lives. The technology that underpins this security and helps to keep our information out of the wrong hands is called cryptography. Cryptography is a critical building block of cybersecurity and today’s increasingly popular digital, virtual money called cryptocurrency. With Bitcoin, the first modern cryptocurrency, recently hitting an all-time high, we wanted to share this guide on cryptography 101 to explain how cryptography and cryptocurrency work and what you can do to increase your organization’s cybersecurity.
In today’s digital age, where sensitive information is constantly being transmitted and stored electronically, secure communications and transactions are a foundation of digital banking, commerce, supply chains, and many other services that we use in our personal and professional lives. The technology that underpins this security and helps to keep our information out of the wrong hands is called cryptography. Cryptography is a critical building block of cybersecurity and today’s increasingly popular digital, virtual money called cryptocurrency. With Bitcoin, the first modern cryptocurrency, recently hitting an all-time high, we wanted to share this guide on cryptography 101 to explain how cryptography and cryptocurrency work and what you can do to increase your organization’s cybersecurity.
Cryptography 101: Understanding Encryption, Decryption, and Secure Messaging
Today, cryptography plays a crucial role in everyday tasks such as banking, shopping, and communication. The first thing to learn in cryptography 101 is that cryptography involves two main processes: encryption and decryption. Encryption is the process of converting plaintext (readable information) into ciphertext (unreadable strings of numbers and letters) using a specific algorithm (mathematical equation) and a key. Decryption, on the other hand, is the reverse process of converting unreadable ciphertext back into plaintext.
Encryption has become an essential aspect of cybersecurity, protecting sensitive data at rest, in transit, and in storage. By encrypting information, businesses and individuals can safeguard their valuable assets from prying eyes and ensure that even if data is intercepted, it remains unintelligible to unauthorized adversaries. So, let’s dive into how cryptography works.
The Two Main Types of Cryptography: Symmetric and Asymmetric
Let’s start by understanding the two main types of cryptography and how they work. First, Symmetric cryptography uses the same key for both encryption and decryption. This means that the sender and receiver must share the same secret key in order to communicate securely. Symmetric cryptography is generally faster and more efficient than asymmetric cryptography, but it poses a challenge when it comes to securely exchanging the secret key. This is often used in closed systems within a bank network or data storage service because it is faster, and the data is not meant to be exposed outside the environment.
Asymmetric cryptography, on the other hand, uses two different keys: a public key and a private key. The public key is freely available to anyone and is used for encryption, while the private key is kept secret and is used for decryption. This allows for secure communication without the need to exchange secret keys. However, asymmetric cryptography is generally slower and more computationally intensive than symmetric cryptography.
Asymmetric encryption is one of the primary methods used to transfer data across a network and through other computers. It is often used for encryption in transit—to protect data as it transfers between two network nodes. For example, if Alice wants to send Sam an encrypted email, she would send it to Sam’s email address. The public key for Sam’s email address is stored on a key server that is used to match the email to the key. When Sam wants to read the message, he uses his private key, which only he has, to decrypt it.
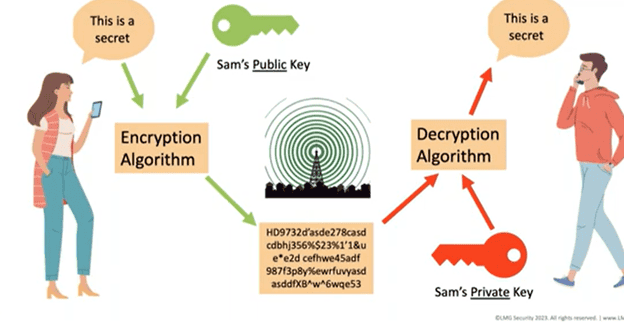
How encrypted messages are sent
Sadly, most organizations don’t have encrypted internal emails, and external emails are not encrypted unless both parties are using the same closed app or system. At LMG Security, we use encrypted internal emails and we highly recommend it! It reduces the risk of phishing attacks since you can easily detect any attacker that tries to pretend to be someone from within your company as any spoofed emails will not be signed. If a hacker does break into your email, all internal emails are encrypted; they can’t steal information and passwords because all they see are strings of letters and numbers unless they have your key. Now that you understand cryptography 101, let’s look at how these technologies are used to make cryptocurrency work.
Understanding Digital Signatures
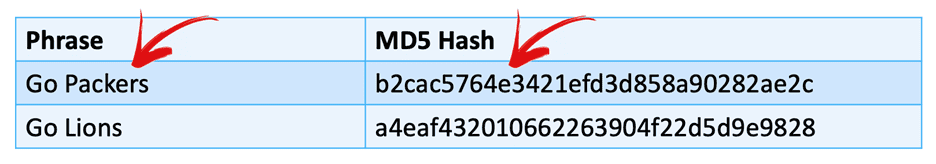
Another key topic in cryptography 101 is understanding digital signatures, which also use asymmetric keys. Digital signatures use cryptographic checksums. Simply put, a cryptographic checksum, or “hash”, is the product of a mathematical algorithm applied to a piece of data. This results in a unique string of letters and numbers as you see in the image below. If you change a piece of the data from “Packers” to “Lions”, it will result in a completely different hash. This enables people to digitally sign documents using a pair of public and private keys to verify authenticity.
For example, If Alice wants to purchase 300 shares of stock, she logs into Sam’s secure program, generates her message, and a hash of the original message is created. This hash is then encrypted with Alice’s private key. On the other end of the transaction, Sam uses Alice’s public key to decrypt the hash and compare it to the message. If they match, then Sam knows Alice sent the message and it has not been tampered with.
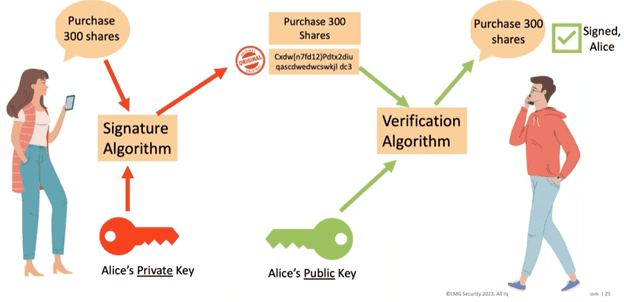
Example of a secure stock purchase message.
How Are Cryptography and Cryptocurrency Related?
Cryptocurrency is a digital or virtual form of currency that relies on cryptography for secure transactions. The first cryptocurrency, Bitcoin, was introduced in 2009 by an anonymous person or group of people using the pseudonym Satoshi Nakamoto. Simply put, Bitcoin and other cryptocurrencies are types of electronic cash that are derived from a chain of chronological digital signatures. The system was created to be anonymous and peer-to-peer, with no trusted financial intermediaries. Designed to be non-reversible and private, cryptocurrency can help keep payments anonymous, facilitate quick international transactions, and help underserved communities that don’t have local banks. In fact, banks are even starting to take advantage of cryptocurrency to speed their transactions.
How are Bitcoins made? Bitcoins are made by using a significant amount of computing power to solve difficult math equations and they are currently rewarded with a new block and 6.25 Bitcoins. However, we are coming up to another Bitcoin halving, so any time now a new block may only be worth 3.125 Bitcoins.
How are Bitcoins sent? Bitcoins use a distributed, chronological, digital ledger that anyone can view. Distributed ledgers that organize the data in blocks and have updates in an append-only structure are called blockchains. The blockchain is composed of different blocks that are linked together with the hashes we talked about earlier that are used for tracking and verification. The linking of blocks allows the transactions and the value of the Bitcoin to be tracked, even if the users are anonymous.
How do you send and receive cryptocurrency? You need a cryptocurrency wallet. This is where you store your cryptocurrency keys (which is what proves you own the currency). The security of your wallet is crucial. If someone accesses your wallet and gets your private keys, they can steal your cryptocurrency.
Let’s look at the process for transferring cryptocurrency. If Alice wants to pay her plumber from her Bitcoin wallet (she has a public/private key pair that proves she owns Bitcoin), she needs to get her plumber’s unique username (which is his public key) to initiate a transaction. The new transaction is verified using the hash and both Alice’s private key and the plumber’s public key. Once these are verified, her plumber owns that Bitcoin.
The Downsides of Cryptocurrency
Cryptocurrency also has a dark side. Its ability to provide fast, non-traceable payment has made it the preferred payment method for criminals. You must also be careful with cryptocurrency. If you forget your password for your cryptocurrency wallet and lose your keys, you will also lose all of your cryptocurrency! You should consider a hardware wallet that stores your keys offline. This makes it harder for criminals to steal your cryptocurrency if they gain access to your devices.
The Bottom Line
Encryption is key (sorry, we couldn’t help ourselves…) to securing your information and transactions. In order to get the full benefits of encryption at your organization, we recommend:
- Using a password manager for secure, encrypted password storage
- Ensuring your cloud systems are correctly configured to take advantage of encryption and digital signing
- Backing up private keys and crypto wallets
- Watching out for expired website certificates, incorrect authentication, or invalid signatures
- Ensuring your entire team has regular cybersecurity awareness training to reduce your risk of a data breach
- Using end-to-end email encryption
We hope this cryptography 101 blog has helped to demystify cryptography and cryptocurrency! Please contact us if you need cybersecurity help. Our expert team is ready to help with a wide array of services from cybersecurity policies and cloud configuration assessments to password manager implementations and employee cybersecurity awareness training.
