3 Ways to Slash Your Supply Chain Ransomware Risk
 With the Colonial Pipeline supply chain ransomware attack creating temporary gas shortages that disrupt local gas stations, airlines, trucking companies and more, you may be justifiably worried whether your organization is doing enough to prevent hackers from disrupting your operations and supply chain.
With the Colonial Pipeline supply chain ransomware attack creating temporary gas shortages that disrupt local gas stations, airlines, trucking companies and more, you may be justifiably worried whether your organization is doing enough to prevent hackers from disrupting your operations and supply chain.
“Cyber extortion has gone through an industrial revolution,” said LMG Security’s CEO, Sherri Davidoff, who was quoted in a Wall Street Journal article about the pipeline attack. Hackers have exponentially increased their capabilities in the past year and ramped up “double extortion threats,” where criminals not only hold data and files for ransom, but also threaten to publish it unless victims pay their demand.
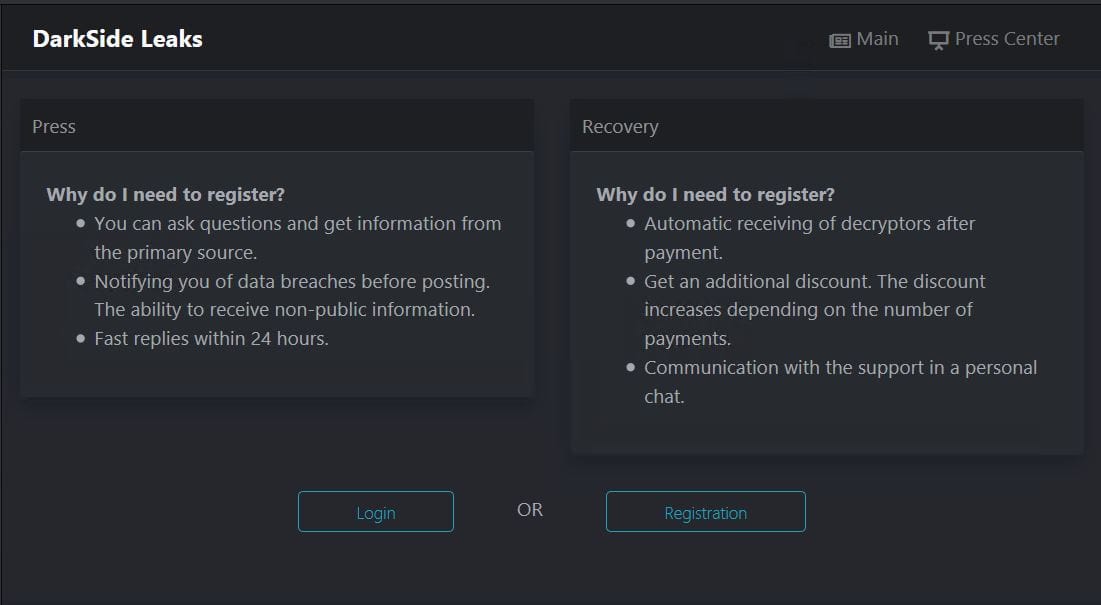
An actual DarkSide login screen. As you can see, hackers have become very professional, and ransomware transactions frequently look like regular business interactions.
Bigger Targets, Wider Ripple Effects
Ransomware is one of the top threats in cybersecurity, and it’s on the rise. According to Coveware, the average ransom demand was $220,298 in the first quarter of 2021. Recently, ransomware operators adopted franchise models, where they provide “partners” with access to sophisticated ransomware-as-a-service infrastructure. The DarkSide ransomware gang, which was implicated in the Colonial Pipeline attack, claimed afterwards that they would vet their partners more carefully “to avoid social consequences in the future.”
Two Different Ways Ransomware Impacts Your Organization’s Supply Chain
There are two different ways supply chain ransomware attacks can disrupt your operations: via a direct attack on a supplier of goods or services, or through your technology supply chain.
- Goods and Services Suppliers – In a direct attack, like the Colonial Pipeline incident, the hackers attack an organization that provides goods or services. Organizations that require 24/7 uptime are particularly vulnerable to attacks on their operations, such as hospitals, ecommerce sites, payment processors, and critical infrastructure suppliers such as Colonial Pipeline. These direct attacks anywhere in your organization’s supply chain can be devastating for your business. According to Coveware, it takes an average of 23 days for organization to recover from a ransomware attack. This sudden outage can cause ripple effects in the supply chain. In addition to the direct costs, the Colonial Pipeline incident highlights the upstream and downstream impacts of disruption and downtime caused by a supplier ransomware attack, as evidenced by the many everyday consumers that are now paying higher prices at the gas pump due to the shortage. This type of attack underscores the potential risk and cost associated with the unseen vulnerabilities of external suppliers.
- Technology Suppliers – Cybercriminals can also attack your technology supply chain, by breaking into cloud providers, software vendors or IT companies. They can use this access to siphon off any data the supplier hosts for you, or worm their way into your environment to deploy ransomware. Two high-profile data breaches – SolarWinds and Accellion – surfaced in late 2020, dominating the news and placing a laser focus on a growing pattern of attacks in the supply chain. Both cases illustrate how vulnerabilities in software vendors’ products and processes can enable criminals to breach customer environments. The vulnerabilities were, in essence, a virtual “one key fits all” that allowed attackers to access and breach any customer that was using these products. In the ongoing Accellion incidents, a ransomware gang took advantage of this access and threatened to leak the victims’ data, in some cases even notifying the press and data subjects themselves.
3 Tips for Managing Supply Chain Ransomware Risks
Your organization likely relies on a plethora of external suppliers for services, software, and devices that are critical to your day-to-day operations. All suppliers pose risk, and the more suppliers you have, the greater your risk of encountering a direct attack or a technology supply chain attack.
Make sure to carefully vet your supply chain vendors and partners to reduce your risk of supply chain ransomware disruptions. Don’t forget about your fourth- and even fifth-party supplier risks. In many cases, third-party vendors rely on fourth-party suppliers such as Amazon or other technology providers to support their services. Each link in the supply chain introduces risk of a supply chain ransomware attack.
Here are a few tips for effectively managing your risk:
- Include Cybersecurity as Part of your Vendor Selection Process. Do you have a supplier vetting program? If not, it’s time to start vetting new and existing vendors. Start with new vendors, and gradually vet existing vendors. Ensure that any software provider you work with has a strong software development security program. Work with your IT team to develop a set of minimum standards each vendor or partner must meet, then develop a vendor vetting process to ensure your vendors and partners meet these requirements. Read our vendor vetting blog for best practices and our supply chain security checklist for additional tips.
- Limit Supplier Access. Cut down on your work and your supply chain security risks by limiting suppliers’ access to your technology resources and sensitive data to what they really need. Often, the focus is more on getting a service in place quickly rather than on whether the supplier is prepared and capable of safeguarding data. Giving your vendors only the minimum access they need is a great way to prevent supply chain ransomware from impacting your environment.
- Involve Key Suppliers in Your Response Planning. When it comes to ransomware attacks, it’s not “if,” it’s “when.” Identify your key suppliers and include them in your cybersecurity response planning and training exercises. Make sure you and your suppliers have both the plans and technology infrastructure to prevent ransomware attacks, as well as the training to triage and minimize the damage in case an attack occurs. Downtime is one of the costly impacts of a ransomware attack. Your supplier’s downtime can impact you, too, so choose suppliers that have plans to minimize downtime in specific situations such as a cyberattack. Do they define a downtime limit or recovery time objectives (RTOs)? Is their support staff available 24/7? Do they have immediate fail-over capabilities to alternate sites if you can’t afford downtime? These are all questions you should consider.
Remember, your organization bears the financial and operational consequences of supply chain ransomware risk. If one of your suppliers experiences an attack, your organization could be impacted by their downtime or worse, experience direct impact to your data. Your organization, not your supplier, may be viewed as responsible in the eyes of your community and customers. We all must work together to prevent supply chain ransomware attacks.
Looking to understand your risk of a supply chain ransomware attacks? We offer a ransomware risk assessment that evaluates your risks and gives you actionable steps to help prevent ransomware attacks. We also offer ransomware response training, so you are proactively prepared. Contact us for more information.
