2023 Cyberattack Trends: Zero-Day Attacks, Virtualization Vulnerabilities & More

2023 Cyberattack Trends
- Zero-day exploits are a top attack vector. It’s not a matter of if you will have a vulnerability, it’s a question of how often. With 55 zero-day vulnerabilities exploited in 2022 and software exploits serving as the initial intrusion point for 32% of attacks with identified causes, cybersecurity and incident response teams have been scrambling. Zero-day exploits are a top target. Attackers search for unknown software vulnerabilities so they can use them to quickly attack organizations and gain access before the victim or the vendor realizes that there is a security gap. If you don’t patch these zero-day vulnerabilities, they become known exploits and criminals will continue to exploit these vulnerabilities for years. Read this Zero Day exploit Prevention and Response Checklist for a deeper dive into zero-day attack trends, details on the new MOVEit attack, and prevention advice.
- Hypervisors are now a very popular target, and attackers have increased their attack intensity and the destructiveness of attacks. One of the cyberattack trends our team has noticed, and confirmed with multiple partners, is that criminals have dramatically increased their focus on attacking virtualization hosts and hubs. BlackBasta, LockBit, Conti, and many others now have encryptors that work specifically on these hosts and employ rust-based malware (that is extremely hard to detect) that can function on multiple operating systems, including Linux-based hypervisors. To make matters worse, Conti’s ESXI encryptor was released in the wild, and many other criminal groups were able to access and modify it. This provided a wide variety of low-level hackers with access to a high-powered cyberattack tool. Hackers are targeting virtualization hosts and hubs because they are widely used, attackers can encrypt your entire critical infrastructure at once, and it makes recovery more difficult.
- Attackers are gleefully using your communication systems against you. If you don’t know your network is secure, you should assume it is not. Attackers are very good at avoiding detection. Even when IR teams are in the system and think they have locked the hackers out, they can persist in the network. Check out the image below from a recent attack. The hackers taunted their victim by publicly posting an image confirming they still had access and that they had watched the victim’s morning IR team video call. This reconnaissance enabled them to hear the recovery plan and take steps to evade detection.
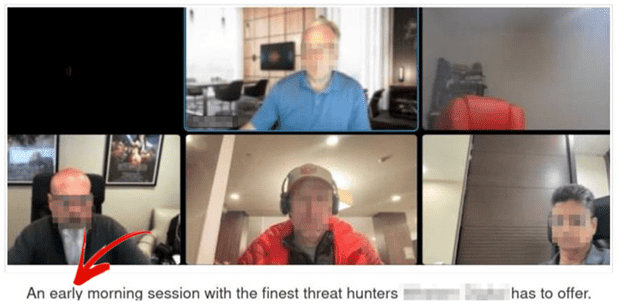
This image was posted on the dark web by attackers as they mocked their victim.
- Attackers are increasingly targeting employee personal devices, elevating BYOD risks. Many employees have been compromised in past breaches and their information and cell phone numbers may be available for free in online databases or for sale on dark web markets. At Black Hat 2022, two researchers found databases with cell phone numbers and stolen passwords for over a BILLION users. Hackers are leveraging this type of information to create highly targeted phishing campaigns hoping to compromise employee personal phones as an access point to your network. Read our blog on mobile security best practices for prevention tips.
- Increased multi-level supply chain attacks such as the recent MOVEit breach. Supply chain attacks usually provide criminals with access to multiple systems, and many suppliers, partners and customers don’t notify each other when they are the victim of a breach. These attacks give criminals the gifts of access and time. While targeting supply chains is not a new cyberattack trend, the playbook for this multi-level attack has changed. This blog on supply chain security best practices provides more information on this cyberattack trend and offers prevention advice.
- MSPs continue to be a high priority target. While this is also not a brand-new cyberattack trend, Managed Service Provider (MSPs) continue to stay on the list of top attack targets. MSPs are a goldmine of customer information and one cyberattack can provide access to many organizations. MSPs have remote monitoring and management tools in place to support their customers. If hackers can compromise an MSP’s remote monitoring and management tools, they may be able to gain instant administrator control over the networks of all the MSP’s clients. If your MSP does not use strong, unique passwords for each client, your risk is even higher.
We hope you found this information on cyberattack trends helpful! Please contact us with any questions or if your organization could benefit from cybersecurity advice or services.
