What To Do AFTER Your Cyber Risk Assessment
Conducting these assessments involves identifying what clients need to protect (i.e., sensitive data, critical systems) and the vulnerabilities and threats associated with those assets. Vulnerabilities and threats are then assessed for likelihood and potential impact of an exploit, taking into account existing security controls (technical or non-technical) that may mitigate or lower the overall likelihood or impact of an exploit.
Turn Your Cyber Risk Assessment Into an Actionable Plan
This blog is intended to provide guidance on using cyber risk assessment results to plan your risk treatment activities, and as an essential component of your organization’s overall risk management strategy. You may also be interested in our blogs on how to get the most from your risk assessment and how to ensure your assessment results are actionable.
What should you do after you get your results? Start with a plan. Ideally, risk levels should be used to support prioritization of remediation activities. This may sound obvious, but many organizations review the whole list (regardless of risk rating) looking for quick wins. We all love quick wins! But if they are aimed at a problem already rated as low risk, your time and resources are likely better spent elsewhere.
Therefore, start your risk treatment planning with any critical and high risks items identified in your cyber risk assessment. These are the items your organization needs to be worried about. Gather appropriate management and staff to review the findings and brainstorm options for risk treatment.
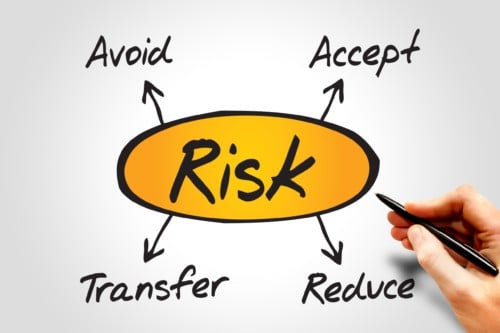
The standard risk treatment options are:
- Avoid the risk by eliminating corresponding activities
- Mitigate the risk by implementing security controls
- Transfer the risk to an external party, i.e. insurance
- Accept the risk
Critical and high risks factors should rarely be accepted and are usually not well-suited to avoidance or transfer without significant changes to your business operations. That leaves mitigation as the most likely focus for your discussion.
How to Prioritize Your Mitigation Plan
Here are some guidelines for evaluating your options and selecting treatment plans.
- Many risks cannot be solved completely. Therefore, your strategy should focus on ways to reduce the risk. Since risk rating is a combination of likelihood and impact, those are the two levers you can pull to bring the overall risk rating down. It is important to consider ways to do both.
- Example: Do gaps in user awareness training make your organization vulnerable to phishing? Improving training is the first fix we think of, which will reduce the likelihood of successful phishing attacks. But also consider impact-reduction measures such as role-based access control, which can limit the scope of malware or ransomware. Improvements in endpoint protection, detection capability, and incident response preparedness can also reduce the potential impact of successful phishing attacks, so consider all options.
- Be sure to consider risk reduction opportunities even if you can’t fully fix the problem in the short term.
- Example: Many organizations feel that moving from an 8-character minimum requirement for passwords to 16-characters is too big a change to do in one jump. But that is not a good reason to leave the requirement at 8. Instead, move to 10 or 12 characters and keep this risk in your register with a planned timeline for incremental increases. Revisit the risk rating as you make changes, as you will be reducing the risk gradually over time. Interested in quantifying password length risks? This blog shows the data and risks for different password length requirements.
- Be careful not to remove or overlook risks that can’t be addressed quickly due to budget or other resources. The risk register should be a communication tool for your organization to help prioritize activities and allocate budget and resources. Keeping risk factors on your radar and creating a multi-year plan to address these risks, is a key factor in the NIST Cybersecurity Framework for increasing your company’s cybersecurity maturity. (For more information on this topic, read my cyber maturity blog.)
- Example: If a lack of incident response testing was identified as a high-risk factor in your cyber risk assessment but a tabletop exercise won’t fit in your budget this year, select it for mitigation with a 2021 timeline for completion. Go ahead and assign an owner, select a target date for submitting the project for budget approval, and select a vendor. Capturing longer-term plans and resource needs in the risk register keeps them on the organizational roadmap for resource allocation.
What About the Medium and Low Risks?
- After you make plans for any Criticals or Highs, the Mediums should be scrutinized for opportunities to further lower your risk, focusing on either with the likelihood or impact levers. Some mediums may also be candidates for acceptance, especially if they have a very low likelihood or impact.
- After you address the Mediums, review the Lows and Very Lows for quick wins, but not if they will take resources away from risk reduction efforts for bigger risks. Also look for candidates for risk acceptance.
When to Accept Risk
- A cyber risk assessment appropriately shines a spotlight on risks that need attention. But don’t forget to look at the flip side – it also tells you where not to spend your time and money.
- But don’t be too quick to accept! Be sure you are accepting risks for the right reasons. It should truly be a decision based on low or very low likelihood, impact, or both. To accept the risk, your organizational stakeholders should agree that your organization can live with the consequences.
- There may be other cases with higher likelihood or impact, where acceptance is based more on the idea that the risk is truly out of your control. But if this is the reason, be sure your team does a serious deep dive to identify any opportunities to reduce likelihood or impact. Try to reduce the risk to a more acceptable level.
- Don’t accept a risk just because something is difficult, whether politically, culturally, financially, or due to staff time or skill set. If these are your reasons, scroll up to the previous section to revisit how to evaluate your risk treatment options.
Regardless of your risk treatment decisions, be sure to document them in a risk treatment plan. Consider adding columns to your cyber risk assessment spreadsheet to capture risk treatment decision (Avoid, Mitigate, Transfer, Accept), planned activities, action item owner, timeline or due date, and current status.
The Secret to Success
Use your risk treatment plan as a communication tool, and share the plan with management for visibility and support. Then, review your organization’s progress regularly to maintain accountability and identify any roadblocks inhibiting progress. If you take these steps, you will be well on your way to reducing risk.
Would you like advice or support assessing or managing risk to your sensitive data and critical systems? Contact us, and our experienced consultants can work through this process with you, to accurately rate risks in your environment and identify realistic, actionable ways to reduce risk and improve your organization’s overall cybersecurity posture.

