How To Search for Strings on a Disk Image Using The Sleuth Kit
While there are plenty of forensics GUI tools that can perform string searches, sometimes you may want or need to locate strings on a disk image using command line tools only. You can efficiently locate strings on an image and extract the files that contain them using The Sleuth Kit, an open-source forensics toolset.
We have a forensic image, img.dd, and need to find out if it contains any credit card data. We could search for the regular expression for a credit card number, but this approach is prone to generating lots of false positives. Instead, we’ll take a first pass by searching for the string “credit card” and hope it points us in the right direction.
The ‘strings’ command will output all the printable characters in the image. In our case, it is important to use the ‘-t’ option, which will print the offset of the strings it finds (we are printing the offset in decimal). Pipe the output of ‘strings’ to ‘grep’ to search for “credit card.” We make the search a little more flexible by ignoring case (with the ‘grep’ ‘-i’ flag) and making the space optional.
strings -t d img.dd | grep -iE "credit ?card"
The search returns one result, at offset 54002688. Good thing we searched case-insensitive with or without a space! It looks like it may be the header row of a CSV file containing credit card data, which merits taking a closer look at this file:
![]()
To map this offset to a filename, we first need to gather some additional information about the image using TSK. Start by running ‘mmls’ on the image:
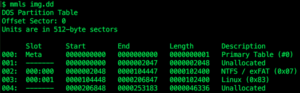
The image has an NTFS file system starting at sector 2048 (byte 1048576) and a Linux file system that starts 104448 sectors (53477376 bytes) in. We need to figure out which file system “CreditCard” is in.
Since ‘strings’ gives us the offset of the string on the entire image, we need to subtract the file system start location from the image offset in order to get the offset of the string in the file system. We will try this on the NTFS file system first. Working in bytes, run expr 54002688 - 1048576 to get 52954112. This is greater than the length of the NTFS file system (52428800), so the string must be in the Linux file system instead.
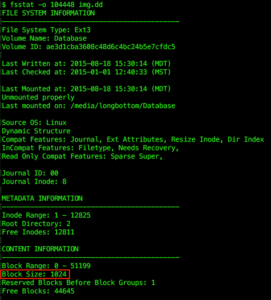
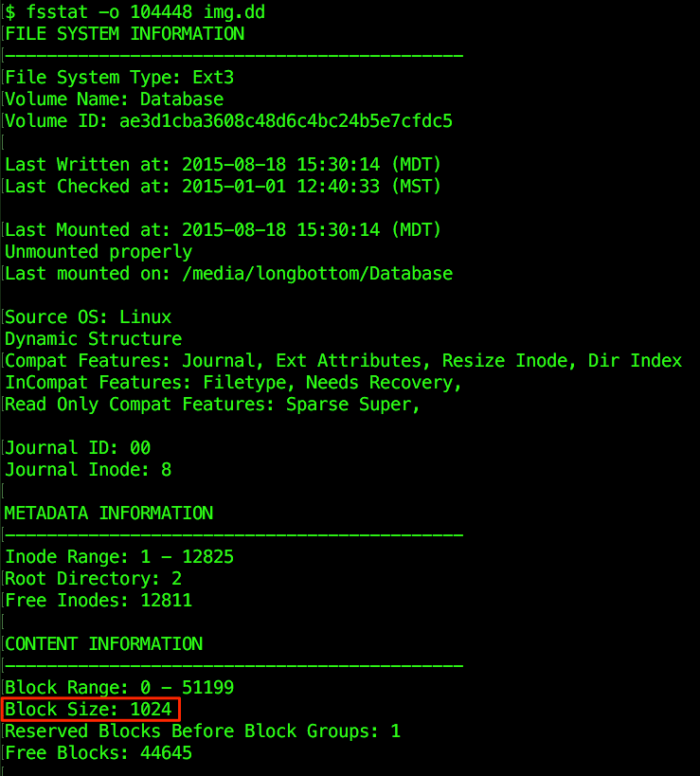
Now subtract the start of the Linux filesystem from the ‘strings’ output offset to get the location of the string in this second file system: expr 54002688 - 53477376 to get 525312. File systems have a value for the minimum amount of space that can be allocated for a file, known as the block size or cluster size. To locate the file, we will specify its block offset instead of the byte offset of the string. To find the block size, run ‘fsstat’ on the Linux filesystem:
fsstat -o 104448 img.dd
The output shows that the block size is 1 KB (1024 bytes). It also auto-detected the file system type as ext3, which is more helpful than the ‘mmls’ output.
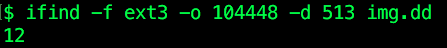
Next, divide the file system byte offset by the block size to get the block number of the string’s location within the file system: expr 525312 / 1024 to get 513. Run ‘ifind’ on the block number to get the inode number of the file containing “CreditCard”:
ifind -f ext3 -o 104448 -d 513 img.dd
This returns 12:
![]()
If we run fls -f ext3 -o 104448 img.dd, we can see that inode 12 corresponds to a file called Customers.csv:
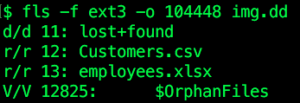
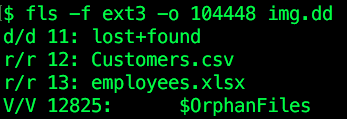
We can run icat -f ext3 -o 104448 img.dd 12 to print the file’s contents, so that it can be saved or piped into other programs as needed.
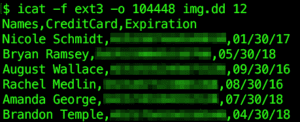
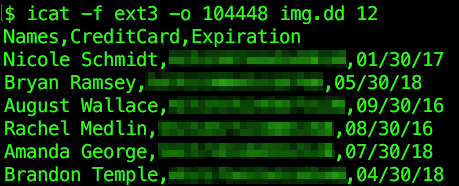
See how LMG can put Digital Forensics to work for you, and feel free to contact us at [email protected]!
