RIP Office365 Magic Unicorn Tool

Yesterday, our team received word that all V1 token access had stopped working, which we were pretty quickly able to confirm as true. This was a disappointing turn of events, but all was not yet lost. Bearer tokens from the Microsoft developer sandbox were still usable and the API was still returning data– until this morning.
We went to pull down a fresh set of test data this morning for some further development of our parsing utility, but instead of a file filled with inbox activities we were presented with the dreaded “403: Forbidden” error, and anyone who has worked in web development knows exactly what that means – the Activities API endpoint was no longer accessible.
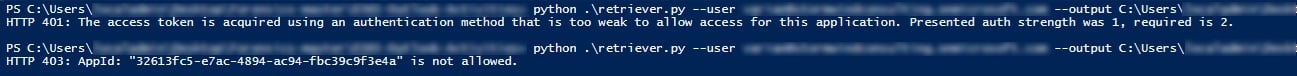
Below is a screenshot of the Powershell output using both a sandbox generated and application generated tokens. The application generated token is returned as too weak for use, and the sandbox token returns a 403 error.

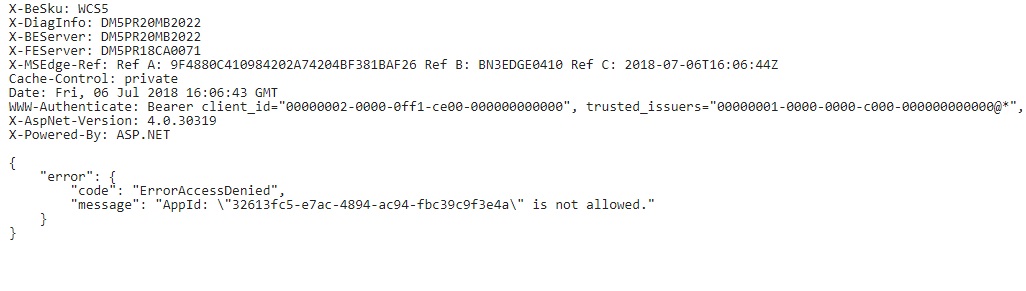
And here is the output from the developer sandbox, which is just a more detailed version of the output from our Powershell testing:

LMG’s search team will continue to test against this and other APIs in our lab, and we will update if there is anything new to add. If you have any further information, contact us @LMGsecurity on Twitter or drop us a line via email.

