How Criminals Are Hacking Printers to Take Over Your Entire Network
 Your printer seems innocuous—but it may be one of your biggest security risks. “Printers are often entrusted with credentials to other resources on your network, like file servers and email servers,” said Tom Pohl, LMG’s Penetration Testing Team Manager. By hacking printers, adversaries can gain access to sensitive data, elevate privileges, and even compromise your cloud environment. In this article, we’ll share Tom’s secrets for hacking printers, leveraging that access, and, most importantly, how to protect your organization from these attacks. Join us as we look closer at the world of printer hacking and how to safeguard your organization from potential threats.
Your printer seems innocuous—but it may be one of your biggest security risks. “Printers are often entrusted with credentials to other resources on your network, like file servers and email servers,” said Tom Pohl, LMG’s Penetration Testing Team Manager. By hacking printers, adversaries can gain access to sensitive data, elevate privileges, and even compromise your cloud environment. In this article, we’ll share Tom’s secrets for hacking printers, leveraging that access, and, most importantly, how to protect your organization from these attacks. Join us as we look closer at the world of printer hacking and how to safeguard your organization from potential threats.
Why Are Attackers Hacking Printers?
Printers are often considered low-risk resources in today’s digital landscape, but nothing could be farther from the truth. “Printers are used to transfer sensitive data from the digital world to the physical world, so a lot of data flows through them.” When documents are scanned, they are often emailed to users and stored in the cloud, too.
Cybercriminals frequently target printers because they have critical access to sensitive information and an organization’s network. Multifunction printers (MFPs) are even more vulnerable, and assuming they are secure because they have advanced capabilities is a common mistake.
Modern printers are controlled using web-based admin consoles. Often, they are configured with default usernames and passwords, which are easy to look up with a quick Google search based on the manufacturer and model. Some printers do not require credentials, so attackers can log in effortlessly and make themselves an administrator. Once inside, attackers have complete control of the printer.
How Attackers Steal Credentials from Printers
Printers need access to network resources to save to shared folders, scan to email, and provide other functions. To facilitate these services, printers are often configured with a domain user account. In fact, according to Tom, “When LMG’s team extracts credentials from a printer, 40% of the time they are domain administrator credentials.” This means that by stealing the printer’s password, a hacker can take over your whole domain.
In order to capture a printer’s password, LMG’s penetration testing team uses “pass-back attacks,” in which the attacker convinces the printer to send a password to them instead of a legitimate server. Tom frequently leverages three primary protocols to capture credentials from printers: LDAP, SMTP, and file shares:
- LDAP Interception
In this first example, Tom will steal credentials from a Konica Minolta printer using LDAP (Lightweight Directory Access Protocol). When a document is scanned and sent to an email address, the printer needs to access the Active Directory or network directory to look up the email address.
Tom gained access to the printer’s administrative console, and then changed the LDAP server address to his own “evil” server. He made sure that the LDAP traffic was configured to be sent without encryption. Then, he used the “test” button to do a lookup. Tom set up a fake LDAP server to receive the credentials. As you can see in the screenshot below, he was able to easily see the printer’s LDAP password in the cleartext traffic.
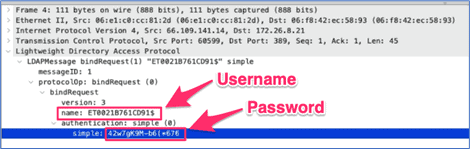
These stolen credentials open the door to other resources on the network and pose a severe security risk, exposing sensitive data and compromising the entire network.
- SMB
Since printers often need to access file shares to save scanned documents, Tom often targets the SMB protocol for hacking printers and capturing passwords. In this example, Tom easily gained access to an HP Color LaserJet printer which had no authentication on the web admin interface. From there, he accessed the scan-to-network folder setup page. The image below shows the HP Scan to Network Folder.
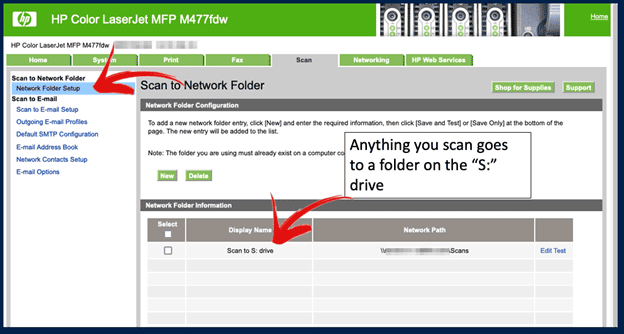
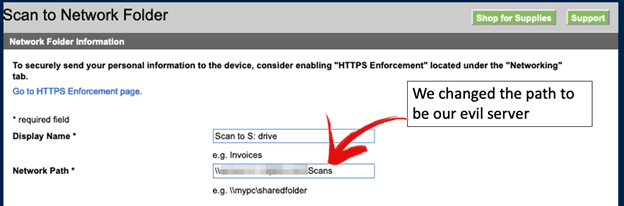
Once Tom was on the setup page, he changed the server’s IP address to his own “evil” host, as shown in the screenshot below. When he clicked the test button, the printer performed an NTLM V2 handshake, a Microsoft protocol that encrypts the password with a challenge. As a result, Tom was able to capture a hash, which LMG’s password-cracking rigs could attempt to crack. In this case, it took about 1 1/2 seconds to crack the password, which was “canon1.”
- SMPT Interception
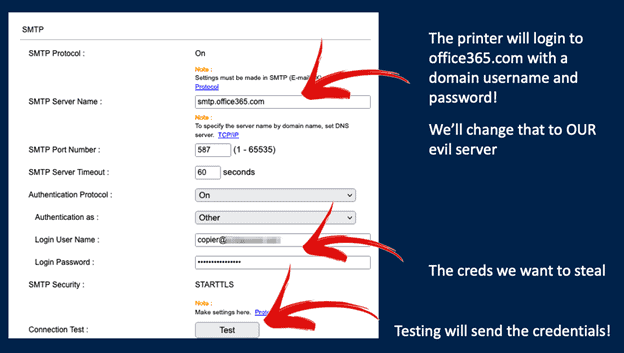
Printers need access to email so they can scan and send documents to users’ email accounts. In this final demonstration, Tom hacked into a Kyocera printer and visited the email settings in the admin console. This printer was already set up to send emails through Microsoft 365. He changed the SMTP server settings on the printer so that it would send emails to his malicious server instead of the legitimate server and also turned off TLS encryption.
As you can see in the screenshot below, you simply need to click a “Test” button to send a test email. The printer connected to Tom’s malicious server, where he used a tool called Responder to capture traffic and log the printer’s Microsoft 365 email credentials. With the clear text username and password, Tom had free rein to access additional resources on the network.
Compromising the Cloud
Next, let’s watch as Tom steals credentials from a Ricoh printer and uses them to escalate to the cloud. After gaining access to the printer’s web admin interface, Tom once again changed the SMTP server’s address to his own, and turned SSL/TLS off, in order to capture the cleartext passwords. This case was trickier, however, because there was no “Test” button.
Fortunately, as you can see in the image below, the printer was low on paper! Tom went into the printer’s settings and turned all the notifications on. The printer quickly sent an email alert—enabling Tom to capture the printer’s password email password.
After gaining access to the printer’s credentials, Tom was able to escalate his attack and gain access to the organization’s Microsoft 365 account. He used the stolen credentials to log into the Microsoft 365 interface and found that it contained scanned copies of all documents that had ever been scanned and sent from that printer.
All the printers within the organization used the same Microsoft 365 account, so that meant that this account contained all documents employees had scanned from any printer in the organization! This attack demonstrates how a simple printer misconfiguration can place large volumes of sensitive data at risk. It also underscores the importance of implementing strong security measures, including encryption and authentication.
Beyond Hacking Printers
An attacker can use similar tactics and techniques that Tom used for hacking printers to access other network devices. For example, Tom has demonstrated how an attacker could exploit similar weaknesses in IoT devices like IPMI interfaces and Crestron room panels to gain unauthorized access to a network. In one case, Tom was able to capture passwords from a Super Micro server by accessing its IPMI and changing the network share address to his own “evil” server. This enabled him to obtain an NTLMv2 hash from the configuration backup. This highlights the importance of securing all devices on a network, including smart conference room devices, camera systems, and more.
How to Protect Your Organization
You can reduce the risk of printer-related security breaches by implementing these six preventive measures.
- Segment your network. Keeping your printers away from unauthorized users is crucial, especially the management interface. This can be done by keeping your printers on a separate segment, accessible only from a limited number of systems as needed. Read on blog on network segmentation best practices for more information.
- Require authentication for printer interfaces. It’s essential to enforce authentication for accessing printer interfaces. Make sure that authentication is required to access the administrative interface. This simple measure can prevent unauthorized access to printer settings and stored credentials.
- Use strong passwords. Weak passwords are a common cause of printer security breaches. Change default passwords immediately and make sure all printers are configured with strong passwords.
- Require encryption in transit. By encrypting passwords and other sensitive data in transit, you can protect printers from interception and tampering. Make sure SSL/TLS are enabled for the web interface, email, and any other protocols. Read Data Encryption Best Practices to learn more about encryption in transit.
- Use app passwords on cloud interfaces. Cloud interfaces for printers can be secured using app passwords. This measure allows organizations to create unique passwords for each app or device needing printer network access. That way, if a password is stolen, hackers are very limited and cannot gain unauthorized access to other resources.
- Deploy Identity and Access Management. Identity and access management (IAM) solutions provide comprehensive visibility into account activity, allowing organizations to detect and respond to suspicious access. IAM solutions can also be configured to send alerts when printer settings are changed, ensuring that security teams know of potential breaches.
We hope this description of how attackers can access your entire network by hacking printers has been eye opening! For more detailed information on hacking printers, watch our YouTube video on this topic. If you are concerned and want to find these security gaps before you are attacked, contact us for a penetration test. Tom and our team of ethical hackers can help you identify security gaps.
