Excel Macro Exploit Teams Up with Emotet Threadjacking

Excel 4.0 XLM macros have been around for decades, but it wasn’t until 2020 that Excel macro exploits began to surge. More recently, Emotet malware payloads are being delivered in contaminated Excel files. Emotet is especially noxious as it can work with TrickBot to enable criminals to steal bank credentials and engage in other nasty activities.
Let’s take a look at this new combination of old threats and what you can do about them.
How Does Threadjacking Work?
Excel macro exploits are now being delivered by threadjacking techniques. Threadjacking (or thread hijacking) is a particularly sneaky form of phishing since it takes over email messages that are part of an ongoing thread. This happens when a Windows host gets infected with Emotet. The initial Emotet infection can originate from a credential dump on the darknet or from a previous phishing attack.
Emotet is more than just malware. It’s actually a blended threat package backed by a cybercrime operation. Emotet has evolved over time to deliver a diverse set of attacks consisting of multiple stages.
After an initial Emotet infection, the trojan can then hack old email messages in a victim’s inbox and even reply to the emails. The real action begins as the attacker sends emails to potential victims within and beyond the affected organization. Reportedly, the entire process takes just under two hours to go from initial infection to completion of the threadjacking email delivery.
The worst part is that thread-jacked emails are replies to legitimate emails. Even worse, the spoofed emails are sent from legitimate, but compromised, email servers. If they can mimic the language used by actual team members, the imposter has a very good chance of convincing victims to enable a malicious Excel macro.
Excel Macro Exploit Must Be Enabled
When Excel 4.0 for Windows was released, Microsoft embedded XLM macros in the application. Through macro worksheets, XML macros can easily automate a multitude of Excel functions. The trick is that you have to enable macros for them to work. Likewise, you have to enable macros on Excel macro exploits for them to be activated which leads to malware installation.
Getting victims to activate macros typically involves a pop-up message when the file is opened. The message may say something like, “Click ‘Enable Editing’ and ‘Enable Content’ to preview this document.” If you received the file in an ongoing email thread, your guard may be down since you think the email is from a trusted source. But clicking would enable the Excel macro exploit to be unleashed.
Here’s an example of what a malicious pop-up message might look like:
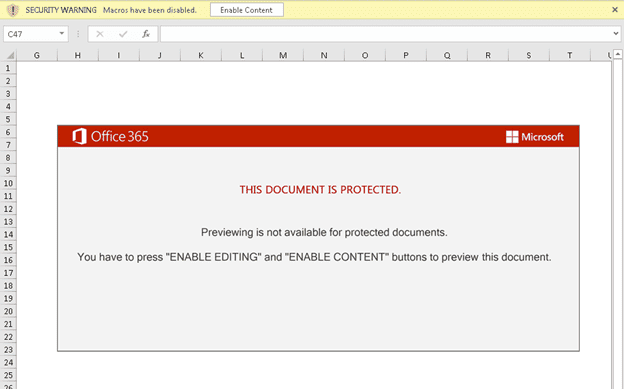
Source: PaloAlto
The Emotet Attack Unfolds
In addition to the initial threadjacking, Emotet enables criminals to commit other nefarious deeds. Emotet started as a banking trojan in 2014, and has evolved to become a full-service multi-threat-delivery mechanism. Emotet associated TrickBot infections can result in bank-account takeover, expensive wire fraud and ransomware attacks.
In more recent cases, Emotet uses a zip archive as an email attachment. They might even provide the password to the zip file in the email. Attackers can also encrypt the file to avoid detection. In other cases, Emotet uses an Excel spreadsheet directly attached to the email.
Once the Excel macro is enabled, Emotet can then execute a PowerShell script. This is a fileless malware attack that takes control of Windows PowerShell tools. This type of attack is especially difficult to detect since it makes use of built-in, trusted software to breach firewalls, run scripts remotely or take over endpoint admin control.
Microsoft Responds by Blocking Macros by Default
Tom Gallagher, Group Engineering Manager, Office Security says, “A wide range of threat actors continue to target our customers by sending documents and luring them into enabling malicious macro code. Usually, the malicious code is part of a document that originates from the internet (email attachment, link, internet download, etc.). Once enabled, the malicious code gains access to the identity, documents, and network of the person who enabled it.”
In response to this vulnerability, Microsoft introduced a default change for five Office apps that run macros. For macros in files obtained from the internet, users will no longer be able to enable content with a click of a button. Instead, a message bar notifies users with a button to learn more. According to Microsoft, the default is expected to improve security against Excel macro exploits.
The security risk warning looks like this:

Source: Microsoft
From there, the Learn More button takes users to a support page titled “A potentially dangerous macro has been blocked”.
How to Reduce Your Risk of Infection From the Excel Macro Exploit
This particular type of cyberattack is extremely difficult to detect since it can come hidden in a genuine, but hacked, email thread. Here are some tips to share with your teams to deter Excel macro exploit attacks:
- Doubt every download: Scrutinize every message connected to any download carefully. Even if it reads a little bit strange (typos, grammar mistakes or odd tone), verify the message with a secure alternative form of communication. Don’t reply to the email directly as the server could be compromised. You can also check out our How to Spot a Phishing Email guide.
- Nobody should ask you to run macros: If you ever get an email asking you to run macros, beware! Asking you to jump through hoops (clicks, zip passwords, etc.) to open any kind of document should set off alarm bells in your head.
- Don’t obey pop ups: If a pop up appears, do not click! Instead, alert your security team immediately, and let them take it from there. If the document doesn’t open in a simple fashion, you could be at risk for downloading malware.
- Prevent PowerShell attacks: Update to PowerShell version 5 as it includes enhanced security capabilities. Also, effective Privilege Management limits who can introduce PowerShell commands/scripts and at what level of privilege.
- Attachment filters: These tools can be used to scan, reject or quarantine attachments. You might also consider running email attachments through a sandbox to test for malicious code.
Threat Sophistication Continues to Grow
Cyberattacks have become more sophisticated than ever. Without a doubt, they will continue to grow in complexity. It makes sense to engage with a cyber security partner that remains up to date with the latest attack trends, and the best methods to thwart them. Contact us if you need help with your cybersecurity testing, policy and procedure development consulting, technical training or incident response.
