8 Cybersecurity Staffing & Training Tips to Turn Your Employees Into a Human Firewall
 Threat actors are upping their game and leveraging AI for more advanced cyberattacks with a special focus on advanced social engineering. The 2024 Verizon Data Breach Investigations Report (VDBIR) found that more than two-thirds (68%) of the breaches and incidents analyzed included a non-malicious human element in the attack. So, how do you protect your organization? The best strategy is to improve your cybersecurity staffing and training practices. Let’s dive into the causes and discuss actionable strategies to reduce your risk.
Threat actors are upping their game and leveraging AI for more advanced cyberattacks with a special focus on advanced social engineering. The 2024 Verizon Data Breach Investigations Report (VDBIR) found that more than two-thirds (68%) of the breaches and incidents analyzed included a non-malicious human element in the attack. So, how do you protect your organization? The best strategy is to improve your cybersecurity staffing and training practices. Let’s dive into the causes and discuss actionable strategies to reduce your risk.
How Cyberattacks Leverage Your Employees
The 2024 VDBIR found that the top two ways attackers target your employees are through credential theft and phishing scams. While traditional phishing, voice phishing, smishing, and QR-code phishing attacks are common, we’re also seeing a rise in AI-assisted deepfakes and AI voice simulation attacks. Social engineering attacks are also becoming more sophisticated and harder to spot, so you need to prioritize your prevention tactics.
But not all attacks are well-meaning mistakes. In the graphic below, you can see that the 2023 Cost of Insider Risks Global Report by Ponemon Institute found that malicious insider attacks caused 25% of human-involved incidents.
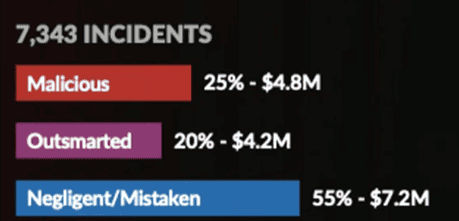
Source: 2023 Cost of Insider Risks Global Report by Ponemon Institute
Criminal groups actively advertise on the dark web and offer to pay employees hundreds of thousands to millions of dollars to deploy malware within their company’s environment or provide them with access information and passwords. These insider threats are very expensive—the same Ponemon report found that organizations with insider incidents faced costs exceeding $18.33 million. So, how do you protect your organization? The best strategy is to improve your cybersecurity staffing and training practices.
Organizational Skill Gaps Increase Your Risk and Potential Breach Costs
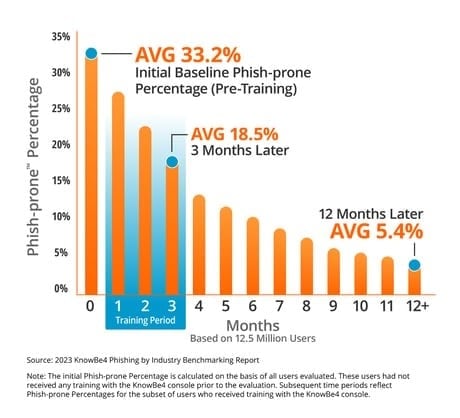
The data is in and strong training programs result in tangible risk reduction and decreases in the average cost of a breach. In the following chart from the cybersecurity training experts at KnowBe4, you can see how regular training dramatically reduces employee susceptibility to phishing attacks. With phishing remaining one of the top causes of a data breach for multiple years, general cybersecurity awareness training remains one of the top ways to reduce your risk of a data breach.
Fortinet also found that 68% of organizations indicate that they face additional risks because of cybersecurity skills gaps. Since trained resources are in short supply, if you can’t add to your cybersecurity staffing headcount due to budget or scarcity of candidates you have two main choices—you can train your existing team (we will share multiple free and low-cost sources later in this blog) or bring in supplemental skills on a fractional or as-needed basis.
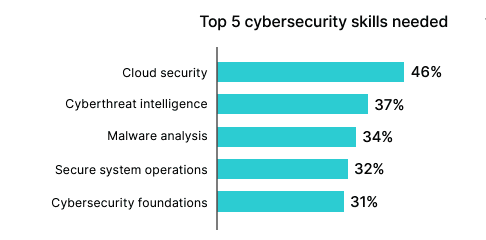
Source: Fortinet 2023 Cybersecurity Skills Gap Report
Finally, how much will cybersecurity training save you in a breach? As you can see in the graphic below, IBM found that having a high level of training in 3 key areas reduces breach costs by over a million dollars.
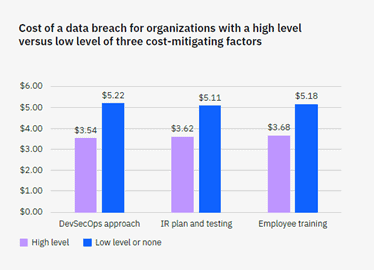
Source: 2023 IBM Cost of a Data Breach Report
Cybersecurity staffing and training can have a real impact on your organization’s risk as well as your bottom line. Let’s dive into what you can do when hiring and training your team to turn them into a human firewall against cyberattacks.
LMG Security’s Top 8 Cybersecurity Staffing & Training Tips to Turn Your Employees Into a Human Firewall
- Refine your hiring practices. When hiring new employees, consider the 3 Cs of trust: Competence, character, and caring. Ensure you are hiring responsible employees who do the right thing. You should implement strong interviewing practices, check references, conduct regular employment reviews, provide performance feedback, and create a company culture where employees feel their organization and fellow team members care about them and are working towards a common mission with shared values. Creating this environment helps employees feel vested in protecting their organization and team.
- Establish a strong security culture. Internal communication is the cornerstone of establishing a strong security culture in your organization. You need to:
- Start with clear policies that are easy to understand and make sense to employees.
- Have regular internal awareness campaigns throughout the year that not only tell employees what to do to keep the organization safe, but also explain why it’s important in terms they understand. When your team understands how an attack can financially devastate an organization, they are more motivated to follow security processes.
- Share examples of the correct behavior and celebrate successes. Praise your team for reporting a suspicious email or verifying unusual requests using a different, known communication method.
- Don’t forget to listen to concerns and feedback. Ensure that employees feel comfortable reporting concerns and know that they will not be criticized for reporting an error.
- Consistently apply corrective actions when needed and appropriate.
- Conduct regular cybersecurity awareness training. Employees not only need to be competent at their job, but they also need to be skilled at spotting general cybersecurity risks. You need to provide regular cybersecurity awareness training for all your employees to teach them how to spot and avoid an attack. We recommend KnowBe4 training, and we also offer managed KnowBe4 training if you wish to outsource the training management function and ensure that a security expert is planning your organization’s training modules and schedule. If you plan to manage your cybersecurity awareness training, here are a few best practices you should follow:
- Use micro-stories. Make your training short, relatable, and memorable.
- Engage your audience. Gamification of training can make it more fun and rewarding.
- Make it accessible. Training should be at least monthly, and it’s also better if it is on-demand to avoid schedule conflicts and ensure both remote and in-office teams can access the training.
- Keep it current. Ensure the content aligns with today’s real-world threats and attack tactics to provide employees with current information so they can spot suspicious activity.
- Use relatable training messages and scenarios. Attendees need to feel it applies to them and understand what to do if they encounter a possible attack.
- Deliver the right training to each segment of your audience. Train your staff and in some cases your customers and community members on how to stay safe. This also requires specialized training for high-risk audiences (finance/accounting, HR, executives, and IT). For more information on role-based training recommendations, read our blog on why cybersecurity awareness training is a top control.
- IT teams need to stay current on cybersecurity threats and prevention techniques. For example, cloud misconfigurations are a top cause of breaches and very expensive for organizations. Appropriate cybersecurity staffing and training is the best way to reduce your risk. Your team should stay up-to-date on cloud configuration best practices and cybersecurity threat prevention, and regularly audit configurations since they change frequently. There are many free and low-cost training sources such as NIST, Isc2.org, NICCS, Fed VTE, Microsoft certifications, AWS Certified Security Specialist, and many others. You can also find local Defcon and Infosec meetup groups that provide valuable training. If you don’t have the time to keep your IT team’s skills up-to-date, you can outsource many prevention services. In this example, you can reduce cloud risks with periodic cloud configuration and security reviews.
- Train several team members on incident response best practices. Remember general IT teams and cybersecurity teams have different skills and experience. Ensure that several people in your organization are trained to quickly identify and respond to cyberattacks. This can dramatically decrease the financial and reputational damage your organization experiences from a breach. If your team needs training, we offer on-demand Cyber First Responder and Ransomware Response classes to affordably train your team to spot incidents, reduce damages, and preserve evidence to comply with cyber insurance or compliance and regulatory requirements.
- Train your team using a tabletop data breach simulation exercise. Incident response tabletop exercises simulate a breach scenario so you can test your incident response plan for gaps and failure points. IBM’s report round that having and regularly testing your IR plan can save you $2.6 million in the event of a data breach. For more information on how to conduct tabletop exercises and our favorite tabletop exercise scenarios, check out our blogs on the best tabletop scenarios for 2024 and evergreen tabletop exercise topics.
- Retain specialized legal expertise. With new breach notification and cybersecurity regulations from the SEC and FTC, proactive cybersecurity laws in over 19 states and territories, as well as HIPAA, CCPA, and GDPR concerns, you need specialized legal expertise to ensure you stay on the right side of the law and avoid hefty fines and penalties. The most affordable approach is generally to outsource this to a fractional legal resource to determine what laws and regulations apply to your organization and provide guidance on how to comply with applicable regulations.
- Hire a CISO or invest in less expensive fractional cybersecurity leadership. An increasing number of regulators now specify that organizations need a designated, experienced cybersecurity leader. However, CISOs and highly skilled cybersecurity leaders are difficult to find and expensive to hire. In good news, you can hire highly experienced cybersecurity leadership on an affordable, fractional basis to fulfill these regulatory requirements. For more information, read our blog on new regulations and how a fractional CISO can meet that requirement.
We hope you have found these tips on cybersecurity staffing and training helpful! Please contact us if you need support with technical testing, expert advisory services, cybersecurity solutions, or training. Our expert team is ready to help!
