Virtual CISO Services: Protecting Your Business from the Ground Up
 Cybersecurity is not just about technology; it’s fundamentally about people. From the boardroom to the server room, everyone plays a critical role. Yet there isn’t enough cybersecurity talent to go around; according to an ISC2 report, the workforce gap grew 12.6% in 2023, with the need for cybersecurity workers dramatically outpacing demand. Cybersecurity leadership can be particularly challenging to find and afford. In this article, we’ll discuss how this people and expertise gap affects your cybersecurity risk and how you can leverage virtual CISO services to shore up your defenses.
Cybersecurity is not just about technology; it’s fundamentally about people. From the boardroom to the server room, everyone plays a critical role. Yet there isn’t enough cybersecurity talent to go around; according to an ISC2 report, the workforce gap grew 12.6% in 2023, with the need for cybersecurity workers dramatically outpacing demand. Cybersecurity leadership can be particularly challenging to find and afford. In this article, we’ll discuss how this people and expertise gap affects your cybersecurity risk and how you can leverage virtual CISO services to shore up your defenses.
How Staffing Affects Your Cybersecurity Risk
“[T]he scarcity of qualified cybersecurity practitioners is reaching alarming proportions,” stated a recent World Economic Forum report. Lack of cybersecurity staff or skills is directly linked to increased cybersecurity risk. For example, adequate staffing in cybersecurity is essential for timely detection and response to threats. Understaffed teams may not effectively monitor all security alerts, increasing the risk of overlooked threats. A report by IBM highlighted that companies with fully staffed cybersecurity teams responded to breaches 27% faster than those that did not.
Finding expert staff is critical for developing and implementing effective cybersecurity programs—especially at the strategic level. A skilled cybersecurity leader brings a wealth of knowledge that helps you prioritize your budget to implement cybersecurity processes and technologies that deliver the most risk reduction, so each year your security gets stronger while staying within your budget. However, expert cybersecurity teams and leadership are hard to find and expensive to hire, so too many organizations are short-staffed. More than two-thirds of leaders reported that “cybersecurity skills shortages created additional cyber risks for their organization,” according to Fortinet. We’re seeing increased demand for fractional services, and our clients share that virtual CISO consulting services have reduced their risks in a shorter time than they anticipated.
Security Leadership: The Keystone of Cyber Resilience & The Rise of Virtual CISO Services
A Chief Information Security Officer (CISO) isn’t just another executive role; it’s a pivotal position within any organization that takes its data security seriously. The necessity of this role was underscored during several high-profile breaches in 2023, including the MOVEit attacks. Companies that lacked strong, proactive security leadership found themselves at greater risk, suffering from extensive data exposure.
The role of a CISO is multifaceted, encompassing the development of security strategies, management of security teams, and ensuring compliance with regulations that may mandate this leadership at the Board of Directors (BoD) level. Virtual CISO services offer a part-time yet high-impact presence to companies who are not ready to commit to or can’t afford a full-time executive position. Last year we wrote about WHY you need a CISO, so this blog will focus on key areas of strategy and risk reduction that a CISO or virtual CISO consulting services generally fills.
- Cybersecurity Leadership and Strategy: CISOs lead the development and implementation of a comprehensive cybersecurity strategy. They align this strategy with the organization’s goals and risk tolerance, ensuring that resources are appropriately allocated to protect critical assets. As cybersecurity leaders, CISOs are responsible for setting the vision and direction for security initiatives across the organization.
- Compliance: Regulations like the New York Department of Financial Services (NYDFS) cybersecurity requirements and the Securities and Exchange Commission (SEC) guidance mandate specific cybersecurity practices and the appointment of a CISO (using virtual CISO consulting services also qualifies) in certain scenarios. These regulations are not just checkboxes for compliance but are designed to ensure that organizations have a strategic approach to managing cybersecurity risks.
- Incident Response and Crisis Management: In the event of a security breach or cyber attack, CISOs are key players in managing the response. They coordinate efforts to limit damage, communicate with stakeholders, and restore normal operations. Effective incident response led by a CISO can reduce the recovery time and costs associated with cybersecurity incidents.
- Establishing a Security Culture and Training: CISOs are instrumental in promoting a culture of security within the organization. They develop and implement training programs to ensure that all employees are aware of and adhere to security policies. This not only helps in preventing human errors—one of the most common security vulnerabilities—but also strengthens the organization’s overall security posture.
A poignant example of the critical need for strong security leadership can be seen in the case of the 2017 Equifax data breach. This breach, which compromised the personal information of approximately 147 million people, was largely attributed to a failure in internal processes and a lack of accountability at the executive level. It highlighted the consequences of inadequate leadership in cybersecurity and underscored the importance of a dedicated and competent CISO or using virtual CISO consulting services.
Why Your Board Benefits from a CISO
Boards of Directors increasingly view cybersecurity risk as a key business risk (and rightfully so!) Over 93% of BoDs ask about cybersecurity, up from 88% the prior year, according to a study by Fortinet.
For the BoD, a CISO serves as a trusted advisor, translating technical jargon into business-relevant insights and ensuring compliance with regulatory guidelines and reporting. The CISO must articulate the organization’s cybersecurity posture, risk exposure, and strategic priorities in a language that resonates with the BoD’s fiduciary duties, strategic objectives, and is aligned with current regulations by SEC, FTC, and others, as appropriate.
A virtual CISO has experience advising multiple BoDs, so you benefit from knowledge gained across organizations and industries. At LMG, our vCISOs can produce a visual scorecard that illustrates the state of your cybersecurity program at-a-glance for easy digestion by BoDs (and executives, too). This enables BoDs to quickly view risk metrics, identify high-level gaps, discuss risk appetite, and ensure proper oversight.
By aligning cybersecurity initiatives with business goals and risk appetite, a CISO or using virtual CISO consulting services enables the BoD to make well-informed decisions that prioritize investment in security controls and resilience measures that investors are increasingly watching.
Your CISO’s Support Team: Expanding Capabilities and Filling Gaps
A CISO alone cannot implement your cybersecurity program, of course. Support is needed at every level, from boots-on-the-ground incident response to executive guidance. Unfortunately, fully staffing a cybersecurity team internally is a challenge due to budget constraints or a lack of available talent.
That’s where outsourced security experts come in. For in-house CISOs, it can also be a relief to have a trusted, outsourced security advisor. Often, CISOs turn to outsourced consultants for expert guidance, advice on compliance with new regulations, and tips gleaned from across many organizations. Newer CISOs often need coaching and training from experts, while seasoned leaders may want support with knotty issues such as breach management or budgetary challenges.
Outsourced security teams can help to quickly supplement your team’s skills and fill gaps, either on an interim basis while you are looking to hire, or as a long-term complement to your internal staff. This approach can also give you access to a wide range of specialized skill sets, such as cloud security, compliance, or vulnerability management—some of the top concerns and cybersecurity skills needed today.
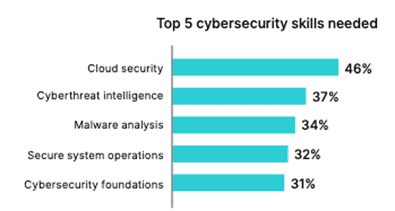
Fortinet research chart on the Top 5 Cybersecurity Skills Needed.
For example, at LMG, our technical team can work hand-in-hand to support remediation efforts after penetration tests and ensure gaps are quickly closed, while reducing the burden on your internal team.
The Bottom Line
As cyber threats continue to evolve, the need for skilled cybersecurity leadership is increasingly critical. Whether you hire a full-time CISO or engage virtual CISO services, skilled cybersecurity guidance not only has a big impact on your organization’s risk posture and bottom line, but is also an essential investment in your organization’s continuity, reputation, and future.
For more information on LMG Security’s technical testing, advisory services (and our virtual CISO services), solutions, and training, please contact us. Our expert team is ready to help!

