The NIST Privacy Framework: Should your Organization Use It to Manage Privacy?
 This post explores the NIST Privacy Framework and highlights some of the benefits it provides for managing privacy risk. Version 1.0 of the framework was released in January 2020.
This post explores the NIST Privacy Framework and highlights some of the benefits it provides for managing privacy risk. Version 1.0 of the framework was released in January 2020.
A Constantly Changing Privacy Landscape
Organizations increasingly have to contend with new privacy laws and regulations, such as Europe’s General Data Protection Regulation (GDPR) and the California Consumer Protection Act. Other laws are certainly on the horizon as well. In fact, U.S. Senator Sherrod Brown recently released a draft bill to protect consumer privacy rights at the federal level. Even if unlikely to pass, the draft bill is indicative of the growing momentum towards more regulation in this area.
In addition, organizations face privacy-related risks that are not necessarily tied to specific laws or regulations such as reputational harm from mishandling data and lawsuits brought under other theories of liability. And, of course, it cannot be forgotten that the main focus of privacy is about the risks to individuals and the harm they could suffer in the event their data is misused or compromised.
Privacy Management Challenges
Several challenges arise when it comes to managing privacy at an organization. These challenges include:
- Efficiently keeping track of multiple requirements from multiple sources, including those found in laws, regulations, and contracts
- Determining how privacy requirements apply to a real-world environment and how to “operationalize” these requirements
- Evaluating numerous process and policy factors: the systems and applications used to collect and process personal data, how data is used and shared, geographic considerations, vendor relationships, written policy requirements, privacy notices, and more
And on top of these challenges, effective privacy management requires the participation of individuals across departments and disciplines (e.g., IT, security, development teams, legal, compliance, HR, and marketing) as well as coordination with external parties, such as vendors and even individual consumers.
Given all these moving parts, where do you even start?
Give Your Privacy Program a Strong Foundation
To help bring order to the chaos, I recommend building a privacy program on a strong foundation. Having a strong foundation can help an organization connect the dots and unify the multiple processes and people involved in privacy management. That, then, makes it easier to organize efforts, measure progress, and provide visibility to others so they can see how privacy is managed.
This is where the NIST Privacy Framework can help. The NIST Privacy Framework was developed through a collaborative effort from individuals in the public and private sector. To be clear, the framework is not a checklist of actions to perform or controls to implement. It is intended to be flexible so that organizations of various types and sizes can use it, which means it is intentionally ambiguous at times. Despite its lack of detail in places, it provides plenty of useful and actionable information.
Why Adopt the NIST Privacy Framework?
The NIST Privacy Framework can serve as the foundation for building a strong privacy program, improving an existing one, or managing other aspects of privacy risk. The benefits of the NIST Privacy Framework include:
Widespread Adoption and Recognition
We at LMG Security are big fans of the NIST Cybersecurity Framework (NIST CSF) as a tool to manage security risk. A big advantage we see with the NIST CSF is that it is widely understood and recognized by government and the private sector.
Although the NIST Privacy Framework is still somewhat new, it’s a safe bet to assume that, like the NIST CSF, it too will have a high adoption rate over time. Choosing a well-known framework provides the organization with the ability to talk about privacy using a common vocabulary with both internal and external parties. It can also serve as a common base for supply chain and partner security discussions. Another advantage with its popularity is the availability of tools and resources tied to the framework, which will continue to increase over time.
A Compilation of Common Privacy Requirements
Many similar requirements appear across privacy laws and regulations. For example, both the GDPR and CCPA cover topics such as de-identification, rights of access, and the use of privacy notices, to name a few. These all appear in the framework.
Although the NIST Privacy Framework cannot account for every possible legal/regulatory requirement, it does at least touch on several common categories of requirements. As such, organizations can map the provisions of various standards, laws, and regulations to Subcategories of the framework to help with compliance-related activities.
Keep in mind that different privacy regimes can cover the same topic but in different ways, so don’t view the framework as a substitute for reading the actual text of particular requirements. Instead, think of it as a tool that can be helpful for compiling and organizing a multitude of different requirements into a single dashboard.
Alignment of Privacy and Security
Perhaps the biggest advantages of all is that the NIST Privacy Framework is structured to align with the NIST CSF. If your organization already uses the NIST CSF to manage security risks, you’ll find that the NIST Privacy Framework has some similarities—and even some overlap in places.
Like the NIST CSF, the Privacy Framework is composed of three parts: Core, Profiles, and Implementation Tiers.
For comparison, the NIST CSF is broken into the following functions:
- IDENTIFY
- PROTECT
- DETECT
- RESPOND
- RECOVER
Meanwhile, the NIST Privacy Framework is broken into these functions (with a “P” added to help distinguish them from those above):
- IDENTIFY-P
- GOVERN-P
- CONTROL-P
- COMMUNICATE-P
- PROTECT-P
The NIST Privacy Framework includes information on ways it can be used in conjunction with the NIST CSF, as shown in this illustration:
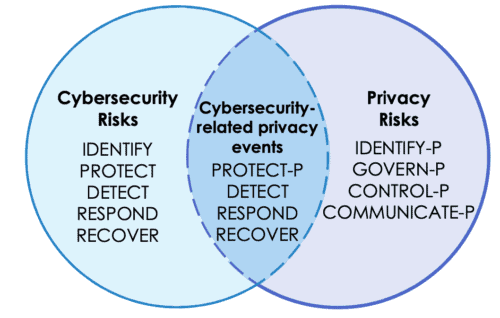
Image courtesy of: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.01162020.pdf
This illustration shows how, for example, Protect-P focuses on risks associated with security-related privacy events (e.g., privacy breaches). To further support managing these risks, the framework says organizations may choose to use Detect, Respond, and Recover Functions from the NIST CSF.
By structuring it this way, those who created the framework recognized that despite the many differences between security and privacy, the two are also interconnected and at times can overlap. For example, both security and privacy focus on topics like asset identification, access control, training and awareness, the use of contractual provisions, and so on. By identifying common ground where there is either direct overlap or where similar activities are involved, organizations can avoid duplicating efforts and improve efficiency when it comes to managing both security and privacy.
(As an aside, if your organization is using ISO 27001 to manage information security, you’ll want to consider using ISO 27701 instead to align security and privacy management).
Conclusion
If your organization is looking to improve how it manages privacy, the NIST Privacy Framework is worth a serious look. The framework is by no means a cure-all and cannot solve all of your privacy-related challenges. But because of the complex nature of privacy and all the moving parts involved, having a solid foundation at the core of your program can go a long way.
If you need help with your privacy program or would like guidance on the NIST CSF or NIST Privacy Framework implementation, contact us. Our expert advisory and compliance consulting team can help.

