Inside the DOJ Crackdown on DarkSide & REvil / Sodinokibi Ransomware Crime Groups

“The Task Force will bring all of the Department’s resources to bear to bolster our all-tools approach and work with our partners here and abroad to combat the threat of ransomware and digital extortion, and to ensure that we hold those who participate in the propagation of these crimes responsible and accountable.”
Some of the biggest attacks and DOJ responses were focused on two major crime groups – DarkSide and the REvil / Sodinokibi ransomware groups. Both of these groups were dominant players in ransomware and conducted some of the biggest attacks in 2021. In addition, both groups utilize a Ransomware as a Service (RaaS) model. Similar to a business franchise, RaaS dramatically expands the number of potential attackers since it enables criminals with little software knowledge to easily launch ransomware attacks. (For more information visit our blog on RaaS.) The affiliate model was a factor in why DarkSide and the REvil / Sodinokibi ransomware were so successful.
In this blog, we’ll dig into the changes in the ransomware landscape, highlight increased enforcement activities, explore what to expect in the coming months, and share what this may mean for your organization.
The Takedown of DarkSide
The DarkSide ransomware gang was started in 2020. This RaaS group attacked Colonial Pipeline in early May of 2021 and was quickly paid a ransom of $4.4 million. A few days later, DarkSide suddenly announced that it was ceasing operations due to government enforcement actions and would release its decryptors. Speculation ran wild wondering if it was really a government takedown or if the ransomware group was trying to avoid paying its affiliates and planning to reorganize under a new name.
Things became clearer on June 7th when the FBI announced that they had earlier been able to reclaim $2.3 million of the Colonial Pipeline ransom by tracking the bitcoin transfers. Since they could prove that this bitcoin was involved in money laundering, they were able to seize it pursuant to “criminal and civil forfeiture statutes.” This ground-breaking announcement marked a turning point in ransomware enforcement and has caused a shift in the ransomware landscape.
In late July of this year, a new ransomware group surfaced by the name of BlackMatter. A review of the code showed that BlackMatter was actually the rebrand of the DarkSide ransomware group, and this group began launching ransomware attacks across the globe. However, in early November—just a few short months after it rebranded—BlackMatter announced that it would also close due to law enforcement pressure. We’ll discuss these enforcement issues more in just a minute.
The US vs. the REvil / Sodinokibi Ransomware Group
Concurrent to the enforcement efforts with DarkSide, the REvil gang, one of the most successful RaaS operations, was executing two of the major data breaches in 2021–beginning with JBS Foods, then onto the Kaseya supply chain attack. On July 13th, soon after the Kaseya supply chain attack, REvil found itself unprepared for the new level of law enforcement activities and ceased operations. While some of the group scattered, in early September of this year REvil returned—reportedly minus one of their leaders. There was gossip over whether this leader, UNKN, had died or disappeared–coincidentally with some of the funds.
Speculation abounded on what would be next for the ransomware group. They began recruiting new affiliates, who they reportedly later left unpaid. But REvil’s return was short-lived. In October of this year, it announced that it believed it had been hacked and again ceased operations. There were reports that UNKN’s keys were used in this hack. Some reports suggest that when they restored their systems from backups, these backups had been compromised. In an interesting twist, several of their affiliates switched their active ransom cases to Lockbit’s platform once REvil went dark. Ransomware has made the transition from a crime that was largely unprosecuted and criminals felt they were untouchable, to a high-risk crime with an aggressive law enforcement response that is impacting even prominent criminal groups.
Law Enforcement Goes on the Offensive
The DOJ crackdown on ransomware continued in early November of 2021. The DOJ took the bold step of offering a reward of up to $10,000,000 for information leading to the identification or location of key leaders in the REvil / Sodinokibi, and $5,000,000 for the arrest or conviction of their affiliates. 
Last week, alleged REvil / Sodinokibi ransomware affiliates Yaroslav Vasinskyi and Yevgeniy Polyanin (from whom the DOJ’s also seized of $6.1 million related ransomware funds) were arrested in what was a big win for law enforcement both domestic and abroad. Both men are accused of attacking multiple US organizations, and Vasinskyi is accused of perpetrating the July ransomware attack against Kaseya. This likely explains the most recent shutdown of the REvil / Sodinokibi ransomware group. On a side note, that same week, a more than 2-year international investigation into the Clop ransomware group resulted in six arrests.
Attorney General Merrick B. Garland spoke about the recent REvil / Sodinokibi arrests last week:
“Together, with our partners, the Justice Department is sparing no resource to identify, and bring to justice, anyone, anywhere, who targets the United States with a ransomware attack. Today, we are announcing that we are bringing to justice an alleged perpetrator of a significant, wide-reaching ransomware attack.”
What This Means for Your Organization
This focused crackdown on ransomware has been seriously disruptive for cybercriminals, and the US promises there are more arrests on the horizon. Ransomware is not the easy money that it seemed to be a year ago. But as Aristotle said, “Nature abhors a vacuum.” While some large ransomware groups are going underground, other groups are considering:
- Focusing on smaller ransoms in the hopes that these attacks are too small to draw the attention of law enforcement.
- Switching to other forms of crime, such as business email compromise.
- Taking a break from ransomware in hopes that the enforcement action will slow. Many larger groups will probably cease operations for a while before rebranding. This may also enable them to escape outstanding payments to old affiliates.
After the news broke about the takedown of the REvil / Sodinokini ransomware group, we were checking RAMP (a Russian dark web forum) to get first-hand knowledge of what ransomware operators where thinking, and some criminals were recommending taking a “holiday” from ransomware attacks, while others were suggesting that with two large ransomware groups shut down, this may be a good time to continue attacks, as long as they keep a low profile.
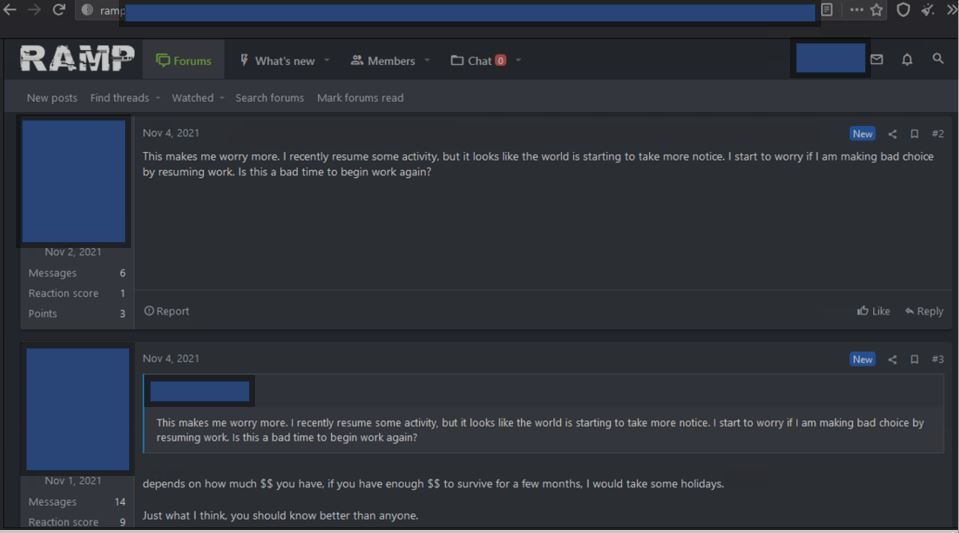
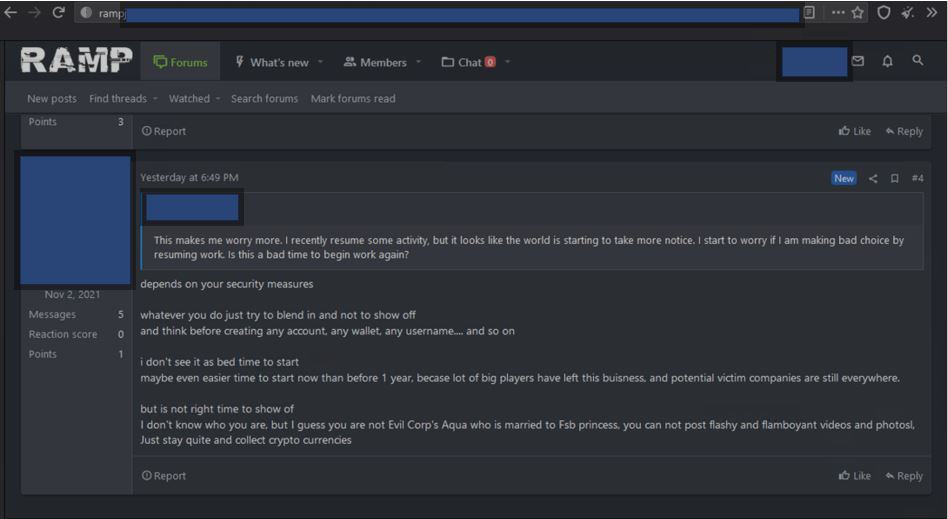
So, what’s next in the US’s burgeoning war on ransomware? The US is focusing on more legislative responses. In fact, our CEO Sherri Davidoff was asked to brief the Senate Committee on Homeland Security and Governmental Affairs about the current ransomware threat landscape. Since we’re all cybersecurity nerds here, we are so excited that our team is playing a part in crafting stronger ransomware legislation!
There was also a new ransomware bill introduced last week. If passed, this new bill will require US financial institutions to share the details of any attacks and ransom requests with the Director of the Treasury Department’s Financial Crimes Enforcement Network. It would further require that US financial organization would have to ask for authorization before they could pay a ransom greater than $100,000, and they would be required to report the payment of smaller ransoms within two days.
It’s a new game out there in cybersecurity and we are fascinated to see what’s next. Organizations should continue to be proactive with ransomware prevention tactics as it is unlikely that ransomware attacks will cease entirely. You can read more on ransomware prevention in this blog.
Contact us if you need help with proactive ransomware prevention services or incident response services. Our team is standing by.
