Five Holiday Scams to Avoid

Here are five threats to watch out for this holiday season:
Infected e-Cards and Memos
Holiday cards can spread cheer—and also malware. Criminals love to send cute Thanksgiving, Christmas and New Year’s e-cards which entice you to click a link— but once you do, your computer is infected with malware that can steal your online banking credentials, credit card numbers and more.
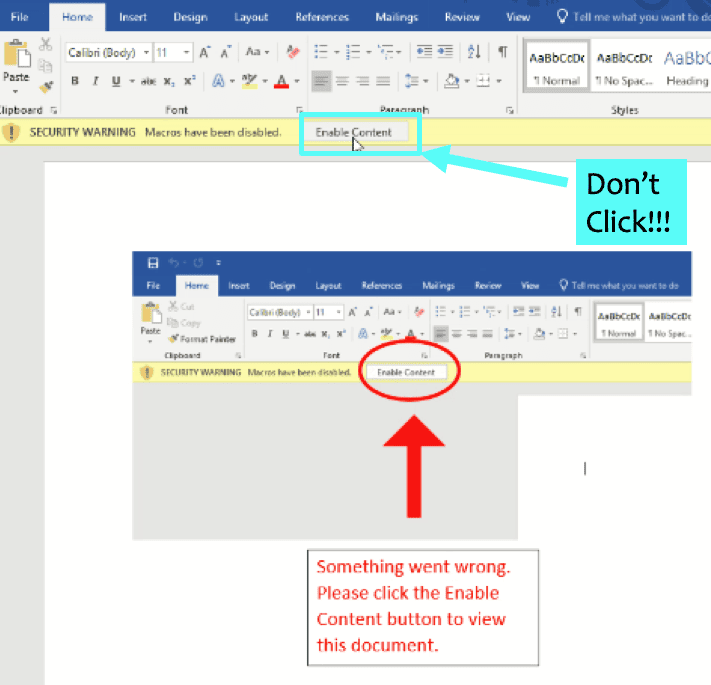
This year, the party started early, when a rash of Emotet-laced Halloween invitations was reported back in October. Recipients were invited to a “Come and say hello to your neighbors and enjoy some food and drink… Details in the attachment.” If you click on the attachment, a Word document opens, prompting the user to “Enable Content.” Once clicked, the malware is loaded onto the victim’s computer.
Days before Thanksgiving, researchers reported a surge of “Thanksgiving lures,” such as a “holiday memo” that announced office closure dates. Busy staff, making their holiday plans, were undoubtedly tempted to click without thinking, and fell victim to these holiday scams.
To protect your staff and colleagues, make sure to provide effective phishing defense training, including simulated phishing emails and regular awareness campaigns. Make sure everyone is familiar with the common “Enable Content” trick shown in the image below, and knows not to click the button.
Fake Retail Deals
Do those Black Friday and Cyber Monday deals sound too good to be true? Cybercriminals love to lure consumers into clicking on fake offers. Often, these phishing email perfectly mirror real email blasts sent by Amazon or other big names. This year, fake e-commerce sites are trendy holiday scams, with researchers reporting a 233% increase compared with last November.
To be safe, don’t click the link— instead, type the store’s address directly into the address bar, and then look for holiday offers on their web site. Remember, if an offer seems too good to be true, it’s probably a scam.
Gift Card Scams
Gift cards are popular, both at home and in the office, as rewards for employees and convenient thank-you gifts for vendors and clients. This makes them a popular target for holiday scams. Criminals take advantage of that by tricking staff into purchasing gift cards and giving them the codes to redeem them. According to the Wall Street Journal, consumers reportedly lost over $74 million in scams involving gift cards or reloadable cards in January-September of this year (an increase of $53 million compared with 2015).
In a typical scam, a criminal impersonates your CEO or another executive, and send emails or text messages to the office manager, executive assistant, or other staff, asking them to purchase gift cards. The cards are supposedly a “reward” for employees or a surprise for the office— meaning that often, the victim is asked to keep the purchase secret. The victim sends the card details to the scammer, who steals them and cashes out.
To protect your team, make sure everyone is aware of common gift card scams, and knows to verify requests from “the CEO” and other managers via phone before responding.
Point-of-Sale and ATM Skimmers
Look carefully at that ATM or point-of-sale terminal before you insert your credit or debit card. Criminals can place “skimmers” to steal your credit or debit card number as you swipe. They can also overlay a keypad to capture any PIN numbers you enter.
Check card readers and PIN pads carefully for unusual signs such as cracks, loose parts or scratches. If you notice anything suspicious, don’t use that machine. Consider using ApplePay, GooglePay, SamsungPay or similar modern payment technologies for retail purchases, since they offer extra security measures that never reveal your card number to the merchant.
E-Skimming
Modern criminals break into ecommerce sites in order to inject snippets of code into the checkout page and steal customer card numbers. These e-skimming attacks (often referred to as “Magecart” attacks) have reached epidemic proportions, affecting retail giants such as Macy’s and Newegg, and prompting warnings from the FBI, US-CERT and others. Criminals have honed their tactics, often targeting popular third-party ecommerce software and plugins, in order to infect thousands of websites at once.
Merchants can defend against this by carefully vetting third-party code that is included in their site. Make sure your software is up-to-date, and stay apprised of any known vulnerabilities in your ecommerce platform. Have your web site tested regularly so that you are alerted to issues early on, before hackers break into your system.
For consumers, e-skimming attacks are a tricky problem, because there is no easy way to detect the malware in web sites that you visit. Carefully consider whether the online shop you use is reputable, and consider using virtual credit card numbers to reduce your risk if a site is infected. If you suspect an ecommerce site is infected, or notice fraud related to an ecommerce sale, report any incidents to www.ic3.gov.
Cybercriminals work overtime during the holidays! Share this list to keep your friends and colleagues aware of holiday scams, so everyone stays safe this season.

