Leaked Zero-Day Vulnerabilities Threaten Us All
 Cybersecurity experts and hackers are in a digital foot race to uncover the latest zero-day vulnerabilities. Zero-day exploits can be used for gaining unauthorized access to systems, avoiding security detection, and stealing data. Day after day, research teams work tirelessly to detect these hidden flaws before they can be exploited by malicious actors. Upon finding a vulnerability, researchers typically notify the organization of the suspected vulnerability, and it begins working on a patch.
Cybersecurity experts and hackers are in a digital foot race to uncover the latest zero-day vulnerabilities. Zero-day exploits can be used for gaining unauthorized access to systems, avoiding security detection, and stealing data. Day after day, research teams work tirelessly to detect these hidden flaws before they can be exploited by malicious actors. Upon finding a vulnerability, researchers typically notify the organization of the suspected vulnerability, and it begins working on a patch.
What if Hackers Steal Zero-Day Vulnerabilities After They Are Reported?
What happens if cybercriminals steal zero-day vulnerability information from software vendors, researchers, or their affiliates? In the recent Kaseya attack, dubbed “the biggest ransomware attack in history”, hackers leveraged zero-day vulnerabilities shortly before the patches were due to be released. Was this a coincidence—or did criminals leverage information about vulnerabilities leaked or stolen from a legitimate party?
In the recent Microsoft Exchange email server hacks, cybercriminals broke into over 30,000 email servers around the world by exploiting a zero-day vulnerability. Suspiciously, the mass exploitation began shortly after Microsoft released inside details to 82 trusted partners through the Microsoft Active Protection Program (MAPP). The information provided to the program members included details of the zero-day vulnerability, the Proof of Concept (PoC) exploit code, and directions on how to reproduce the attack. The cybercriminals’ code noticeably resembled the original proof-of-concept code that was provided to Microsoft by a security researcher, Orange Tsai. The malicious web shell even included his signature password “Orange” which he had hard coded into the sample exploit before alerting Microsoft. According to the Wall Street Journal, Microsoft opened an investigation into whether hackers gained access to the exploit through the MAPP partner program.
This isn’t the first time Microsoft partners have leaked zero-day vulnerability information to hackers. In 2012, Microsoft banned the Chinese security software firm, Hangzhou DPTech, from the MAPPs program due to violation of a non-disclosure agreement. Reportedly, Windows vulnerability proof-of-concept code that had been shared with Hangzhou DPTech was found on a Chinese hacker forum and used to exploit systems in the wild. After Microsoft’s investigation, the company was linked to the incident and kicked out of the program for leaking the PoC exploit code.
The Market for Zero-Day Vulnerabilities
Currently, zero-day vulnerabilities can be purchased on the Dark Web in forums and darknet marketplaces. Age, capability and platform all determine the value of the vulnerability for sale. For example, earlier this year, a Zoom zero-day exploit was found on a dark market listed at $500,000. The LMG Security Dark Web research team spotted several vulnerabilities on hacker forums and popular darknet marketplaces. The images below show a current listing for the Remote Execution Code (RCE) for a Citrix zero-day vulnerability and the previously mentioned Microsoft Exchange hack.
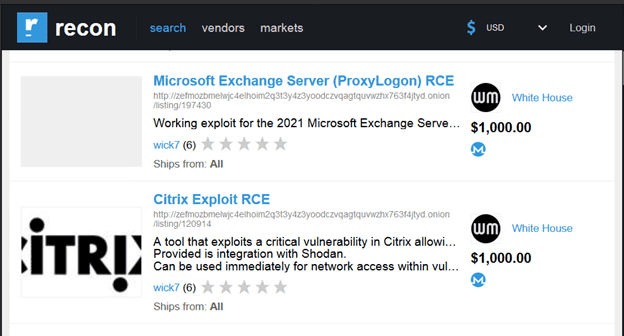
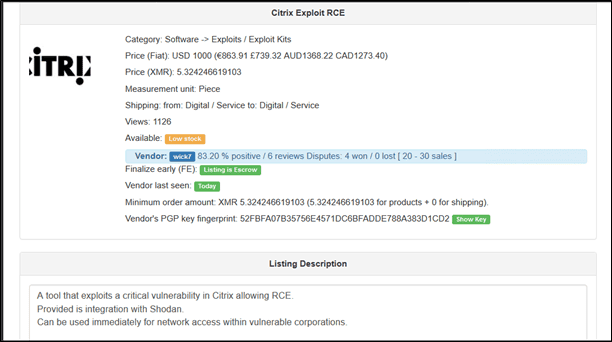
In another example, the image below is taken from a popular hacker forum. This user was attempting to sell a variety of zero-day vulnerabilities. The user goes into detail on what the prices are for each vulnerability he is offering.
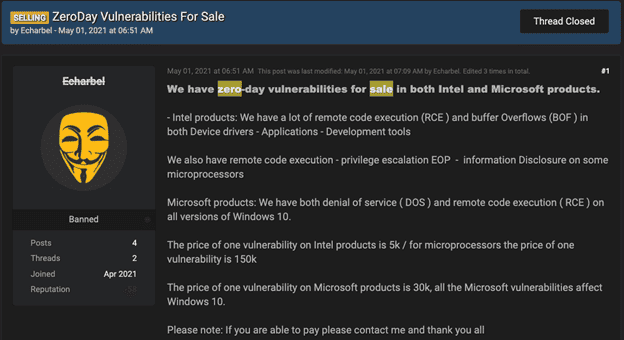
In addition, software vendors also drive the market for vulnerabilities. Microsoft’s largest bug bounty award is currently listed at $250,000. Professional bug bounty hunters can reap millions of dollars by finding and reporting bugs to technology vendors. The zero-day vulnerabilities market offers lucrative financial opportunities for both ethical and criminal hackers.
How Secure Are Bug-Tracking Databases?
How secure are researchers—and technology firms themselves? There are few, if any laws requiring researchers or software companies to publicly report a hack involving a bug tracking database or software source code. For example, in 2017, former Microsoft employees revealed that hackers had broken into the technology giant’s bug tracking database, but the incident had never been publicly reported. This gave hackers access to a digital treasure chest of potentially exploitable vulnerabilities, but the public was never informed.
Stockpiling Zero-Day Vulnerabilities
China, which was recently blamed for the Microsoft Exchange mass exploits, is actively stockpiling zero-day vulnerabilities. According to TheHackerNews.com, Chinese authorities will soon begin requiring zero-day vulnerabilities to be reported to government officials within 48 hours. It will also prevent the collection, sale, or publication of vulnerabilities.
Source code is also valuable because hackers can comb source code to identify new vulnerabilities, and then create zero-day exploits. Chinese state-sponsored actors have reportedly targeted source code of major technology companies for over a decade. For example, in the Operation Aurora attacks, Chinese hackers specifically targeted software engineers and source code management products, which, according George Kurtz, chief technology officer of McAfee, were “underprotected and not very well monitored.” Technology companies targeted in the Aurora attacks included Google, Adobe, Rackspace, Symantec, and many others.
The Future of Vulnerability Sharing
Change is in the air as the U.S. government introduces new regulations that impact technology suppliers. For example, the new executive order removes contractual barriers that may limit companies from sharing information pertaining to data breaches that could impact government networks. This will force certain organizations that experience data breaches to report them within three days. The executive order also mandates that security vendors provide a Software Bill of Materials (SBOM) for critical software. This will provide cybersecurity experts with the opportunity to review the code for potential exploits and assess the security levels of critical software.
Takeaways for Limiting Your Organization’s Risks
- Track your software assets and identify key software products.
- Understand your vendors’ policies regarding disclosure if they get hacked.
- Keep an eye out for new contractual clauses that you can leverage with your vendors.
- Monitor for alerts regarding new zero-day vulnerabilities. Hackers often exploit these during weekends or evenings, so be prepared to act quickly in the event of a new zero-day vulnerability.
- Know your policy regarding emergency patches. Will you apply emergency vendor patches right away, or do you have a vetting process? Discuss this in advance.
We hope you find these tips helpful! Please contact us if you need additional support developing your cybersecurity policies and procedures or if you experience a cybersecurity incident.

