Introducing “NTLMme.py” – Our New, Free Python NTLM Hash Generator Pentest Tool
 Necessity is the mother of invention; last month I created a new NTLM hash generator pentest tool to meet a specific need, and I’ve decided to share it. This will be the first of a two-part series. Stay tuned for part two of this blog that will release additional functionality for this NTLM hash generator tool!
Necessity is the mother of invention; last month I created a new NTLM hash generator pentest tool to meet a specific need, and I’ve decided to share it. This will be the first of a two-part series. Stay tuned for part two of this blog that will release additional functionality for this NTLM hash generator tool!
The Basics on Hashing
Hashing is a one-way cryptographic function, and although hashing is often confused with encryption, they are in fact very different. Encryption is generally reversible, that is, as long as the encryption key is known the data can be decrypted. Hashing cannot be reversed. To determine the cleartext that produced a hash we have to first hash something, in this case passwords, and then compare that hash to the known hash. If they match, we know we have the correct password, otherwise we know our password guess is incorrect.
New Technology LAN Manager (NTLM) hashes are used for authentication “under the hood” in Microsoft Windows systems. I recently had the need for multiple different NTLM hash data sets to perform some analysis related to GPU-based NTLM hash cracking.
A New NTLM Hash Generator Pentest Tool is Born
I could have gone and searched for existing data sets that met the various criteria I wanted to use, but that likely would have involved a decent bit of spelunking git repositories to find exactly what I was looking for. Then once I’d found something that would have worked, I would have had to either trust that the unhashed strings that produced those hashes actually met my predefined criteria, or spend time cracking the hashes for confirmation. Rather than waste time trying to find or massage a data set to meet my needs, I wrote a Python3 NTLM hash generator that would do the trick. Enter “NTLMme.py”!

NTLMme.py currently has three functions, though I have plans for more and will be adding additional functionality to the script soon! For now, though, my new NTLM hash generator tool has single mode, random mode, and input file mode – which will process properly formatted text files.
NTLMme.py Single Mode
In single mode, a string can be provided as an argument with either the “-s” or “--single” flags. The script will hash the string and return it via stdout.
Single mode is useful when you want to quickly obtain the NTLM hash of a specific string (password), maybe for use in a Pass-the-Hash (PtH) attack, simply to validate the hash of a password, to test the efficacy or likelihood of hash cracking techniques, or maybe even to search an NTDS.dit database for a known cleartext password.
![]()
NTLMme.py Random Mode
In random mode, the script will generate as many random NTLM hashes as the user specifies. Random mode is called with the “-r” or “--randomhashes” flags followed by the number of hashes to produce. Random mode creates random 32-character hexadecimal strings. These hashes are truly random as the unhashed string is not known.
Random mode is useful for quickly generating a large number of NTLM hashes that can then be used to stress test or tune the performance of your hash cracking rig.
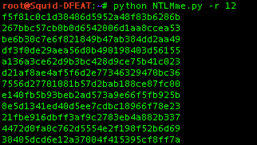
NTLMme.py Input File
Input file mode is called with the “-i” or “--inputfile” flags, followed by the path to the text file containing the strings to be hashed. The text file should contain one string per line without additional control characters. If incorrect hashes are being calculated, it is likely that the text file is not formatted correctly. The script will hash each line of the text file and print the output to stdout along with the original unhashed string in the format of “hash:unhashedString”.
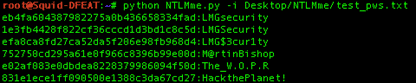
All of these functions support writing output to a file rather than stdout using the “-o” or “--outputfile” flags. Writing the output to a file will automatically create the target text file. However, if the file already exists, the data will be appended rather than overwriting any existing file contents.
![]()
The script is producing 32-character hex strings, but let’s perform some validation to confirm that when these hashes are cracked, they actually result in the original string. For this validation, our test strings will be:
- LMGsecurity
- LMGSecurity
- LMG$3cur1ty
- M@rtinBishop
- The_W.O.P.R
- HackthePlanet!
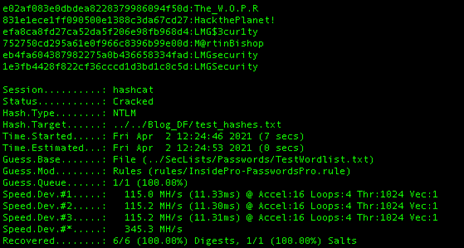
First, I seeded a wordlist by adding these 6 strings to the rockyou.txt wordlist. Then using my favorite password-cracking utility, Hashcat, I ran a dictionary attack with the InsidePro-PasswordsPro ruleset. Expectedly, Hashcat cracked all six hashes and the cleartext strings matched our test strings, which means NTLMme.py is producing the correct NTLM hashes.
As I mentioned, I have plans for additional functions to my new NTLM hash generator tool and will be releasing a blog post when those become available. In the meantime, this script is available on LMG Security’s Github at https://github.com/LMGsec/NTLMme.
Finally, in yet another upcoming blog post I will elaborate on the NTLM hash cracking analysis that influenced the creation of this NTLM hash generator script. In the meantime, contact us if you would like us to handle your pentesting. We have an expert team that is ready to help!

